
Louis DeNicola is freelance personal finance and credit writer who works with Fortune 500 financial services firms, FinTech startups, and non-profits to teach people about money and credit. His clients include BlueVine, Discover, LendingTree, Money Management International, U.S News and Wirecutter. You also have the right to add a fraud alert to your credit reports.
- Interested new affiliates must first get approval from the group’s Telegram channel, which currently has around 2,500 active users.
- The dark web is a network of websites where people can share information anonymously.
- Tracker apps offer a powerful way to keep tabs on credit card activity.
- Digital transformation has increased the supply of data moving, and data breaches have scaled up with it as attackers exploit the data-dependencies of daily life.
- Another study by Fortra’s PhishLabs, a cybersecurity expert, discovered that 81% of cybercrime is stolen credit card data, while financial institutions like credit unions, banks and payment services remain the biggest target of scammers.
- Chase gives you access to unique sports, entertainment and culinary events through Chase Experiences and our exclusive partnerships such as the US Open, Madison Square Garden and Chase Center.
Current Moon Phase: August 29, 2025
Also, learn about the common tricks scammers are using to help you stay one step ahead of them. If you see unauthorized charges or believe your account was compromised contact us right away to report fraud. With Chase for Business you’ll receive guidance from a team of business professionals who specialize in helping improve cash flow, providing credit solutions, and managing payroll. Choose from business checking, business credit cards, merchant services or visit our business resource center. Research by VPN provider NordVPN of over four million credit cards for sale on the dark web found that credit cards from US citizens were the most common, with 1.6 million of the 4.5 million analysed being from the US.
Enterprise Passwords Becoming Even Easier To Steal And Abuse
Stay one step ahead of cybercriminals—use PureVPN’s Dark Web Monitoring to check if your credit card details are being traded on the dark web and protect your identity before it’s too late. Compromised online accounts can also lead to your credit card information being published on the dark web. A compromised online account is an account that has been accessed without the permission of the person who owns it. Accounts are often compromised due to weak password practices like using short passwords or reusing passwords across multiple accounts. They also abuse promos, costing U.S. retailers $89 billion in 2021.
NASA Puts Asteroid Bennu Under The Microscope Space Photo Of The Day For Aug 29, 2025
The Credit People’s Credit Report Repair service is relatively affordable compared to other programs in the space. Even the most basic package (the standard package) includes unlimited challenges to all three credit bureaus. Upgrading to the premium package includes escalated disputes and monthly credit score reports and score refreshes. The hack allowed miscreants access to sensitive information including encrypted passwords, email addresses, mailing addresses, phone numbers and dates of birth. Financial information, including data on PayPal accounts, was stored on separate system and therefore not affected by the breach.
Common Methods Used By Scammers To Steal Credit Card Data
The May 2025 DDoS was launched by an IoT botnet called Aisuru, which I discovered was operated by a 21-year-old man in Brazil named Kaike Southier Leite. This individual was more commonly known online as “Forky,” and Forky told me he wasn’t afraid of me or U.S. federal investigators. Nevertheless, the complaint against Foltz notes that Forky’s botnet seemed to diminish in size and firepower at the same time that Rapper Bot’s infection numbers were on the upswing. The government says Rapper Bot consistently launched attacks that were “hundreds of times larger than the expected capacity of a typical server located in a data center,” and that some of its biggest attacks exceeded six terabits per second. The control panel for the Rapper Bot botnet greets users with the message “Welcome to the Ball Pit, Now with refrigerator support,” an apparent reference to a handful of IoT-enabled refrigerators that were enslaved in their DDoS botnet.
Marijus Briedis, CTO at NordVPN, said the details for sale on the dark web are increasingly acquired through brute-forcing. Request a demo to see how 1Password combines workforce identity, application insights, device trust, and enterprise password management in one place. Sign up to receive exclusive access to product drops, company news, and more.
If You Don’t Already Have A Generative AI Security Policy, There’s No Time To Lose
When there’s a fraud alert on your report, creditors can see that you might be the victim of identity theft and are instructed to verify your identity or contact you before extending credit in your name. ⁴ Child members on the family plan will only have access to online account monitoring and social security number monitoring features. Not only will this give you a head start on canceling and closing impacted cards or accounts — it can also limit your liability if scammers manage to access your funds.

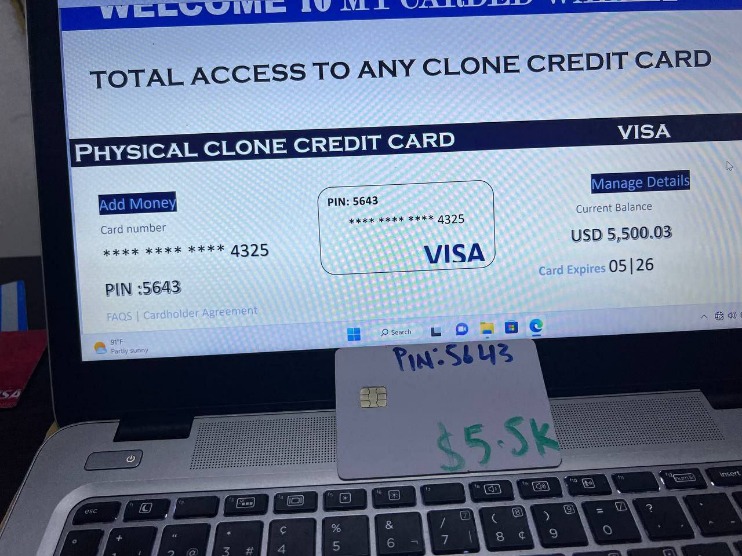
Unmasking The Underground: Navigating The Threat Of Dark Web Credit Card Marketplaces
We have a huge range of products in different styles, from vintage dressing tables to modern kitchens. We also take care of those little details that make all the difference – that’s why our home accessories range includes rugs, candles and photo frames to give the final touch to your décor. A search at DomainTools found has been registering one-off phishing domains since at least 2012. At this point, I was convinced that some security company surely had already published an analysis of this particular threat group, but I didn’t yet have enough information to draw any solid conclusions. A reader who works in the transportation industry sent a tip about a recent successful phishing campaign that tricked an executive at the company into entering their credentials at a fake Microsoft 365 login page. From there, the attackers quickly mined the executive’s inbox for past communications about invoices, copying and modifying some of those messages with new invoice demands that were sent to some of the company’s customers and partners.
- Its focus on financial fraud and high-value transactions has attracted a dedicated user base, contributing to its growing reputation and market value.
- The missives include a link to a phishing page that collects the customer’s username and password, and then asks the user to enter a one-time code that will arrive via SMS.
- Postal Service or some local toll road operator, warning about a delinquent shipping or toll fee that needed paying.
- No, credit monitoring services may trigger soft inquiries on your credit reports, they’re only for informational purposes and don’t impact your credit score.
- Stolen credit cards are used to cash them out or make purchases that can be resold.
MFA is a security measure that adds additional authentication to your online accounts by requiring you to provide one or more forms of verification. Even if a cybercriminal knew your password, MFA would prevent them from being able to log in to your account. Once fraud is detected, a business must act immediately by contacting any customers who may have been impacted and contacting the payment processor to report the fraud.
On This Day In Space! Aug 29, 1965: Gemini 5 Breaks Spaceflight Duration Record
There are several free credit monitoring services on the market, but these generally come with less robust features than paid products. Many do not monitor all three of the major credit bureaus and fail to provide as much identity theft insurance as paid services. Likewise, many credit card companies offer credit monitoring as part of their card services, but many only monitor one bureau or don’t offer services beyond score alerts. Abacus Market appeared on the scene in 2021 and quickly became one of the heavyweights among English-speaking markets on the dark web. The categories are well organized, ranging from drugs and fraud to digital products, guides, and malware.What really sets it apart is its focus on security and usability. It supports PGP encryption, two-factor authentication (2FA), alerts against fake sites (antiphishing), and a verification system for sellers.
Use multifactor authentication to prevent threat actors from guessing at weak passwords, or getting into your systems with a brute force attack. MFA and strong password requirements will force your employees to use strong passwords and change them often. Use encryption to protect customer data and secure your payment processing system. The more secure your information is, the less likely it will be to fall into the hands of a threat actor. Once they had access to the victim’s account info, scammers would estimate their wealth to gauge the types of purchases they could make with the card. The first leak offered only the information contained in magnetic stripes of compromised cards, while the latest sale includes fullz – card number, expiration date, CVV/CVC, cardholder name, and extra personal info.
Automatic payments get declined, travel plans get disrupted, and sorting everything out with the bank can take hours. When fraudulent transactions occur, merchants frequently end up eating the costs through chargebacks. Protect your MSP organization, your end customers and add new revenue streams. The phrase “dark web” conjures images of illegal activity, but it simply refers to the encrypted part of the Internet that isn’t indexed by search engines.

In the relentless battle against cyber threats, financial institutions must deploy proactive strategies and technologies to mitigate risks and protect customers, especially in the context of compromised credit card feeds. Additionally, securing transactions with a 3-D Secure ACS (Access Control Server) solution plays a pivotal role in bolstering the overall fraud prevention strategy. When it comes to credit card fraud, the best offense is a strong defense.
Hackers sold access to the data for as little as $7 via a WhatsApp group. Despite warnings from security researchers and tech groups, it took Indian authorities until March 23, 2018, to take the vulnerable access point offline. Information from the database might be abused for anything from large-scale phishing, industrial-scale fraud, state-sponsored intelligence gathering, and more. The exposed instance was quickly taken down shortly after its discovery, frustrating the researchers’ efforts to identify its source. Identity Guard stands out by offering customers a dedicated customer support manager, plus other helpful tools. Our editors are committed to bringing you unbiased ratings and information.



