
Additionally, the Dark Web serves as a haven for those in censored environments, offering access to restricted information and enabling the free expression of opinions. On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity. Despite its negative reputation, not all activity on the dark web is malicious; some users rely on it as a tool for freedom of expression or to circumvent restrictions. Like the regular surface web, the dark web offers its own social media sites and web forums.
Protect Your Personal Data
He has expertise in cyber threat intelligence, security analytics, security management and advanced threat protection. Prior to joining CrowdStrike, Baker worked in technical roles at Tripwire and had co-founded startups in markets ranging from enterprise security solutions to mobile devices. He holds a bachelor of arts degree from the University of Washington and is now based in Boston, Massachusetts. Knowing if your information is on the dark web is a critical part of protecting yourself from threats.
Everything else on the internet is located on either the deep web or the dark web – and they aren’t as easily accessible, or as safe. So if you’re planning on accessing the dark web, here’s all you need to know to access it safely. While the Tor Browser is designed to protect your privacy, it’s not 100% safe on its own.
Step 3: Connect To The Tor Network
Even with Tor and a VPN, you’re not fully protected unless you also lock down your behavior. Most dark web leaks happen when users skip basic safety steps or reveal too much without realizing it. Use the tips below to patch common blind spots and avoid easy-to-make mistakes. Don’t download anything unless you’re absolutely sure it’s safe.
Quick Guide: Access The Dark Web Safely In 3 Steps

So if you’re ultra-paranoid about tracking, this one’s best reserved for lighter, less sensitive sessions. Encryption-wise, it uses AES-256, and the free version still includes strong tunneling protocols like WireGuard and IKEv2/IPSec, so you’re not stuck with outdated security. If you’re looking for a 100% free VPN with unlimited data that respects your anonymity and doesn’t act shady under the hood, Proton is your best bet. Not all VPNs are built to survive the dark web, especially the free ones. You need tight privacy, strong encryption, and enough server reliability to tunnel through Tor without speed drops or sketchy disconnects.
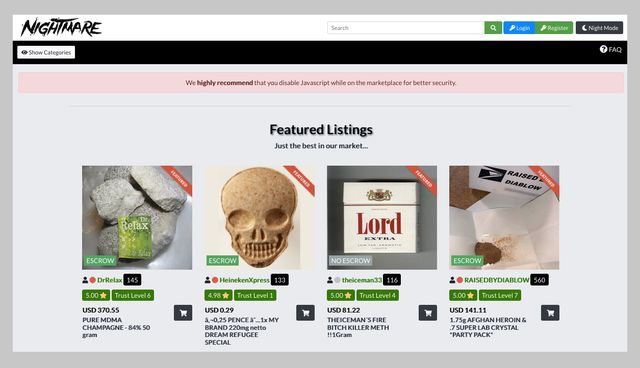
The Best Dark Web Search Engines In 2024
Unlike Tor, however, it cannot be used to access the public internet. It can only be used to access hidden services specific to the I2P network. I2P cannot be used to access .onion sites because it is a completely separate network from Tor. Instead, I2P uses its own brand of hidden sites called “eepsites”.
- The dark web isn’t only about illegal activities; it is specially designed to provide maximum anonymity by making your connection private online through encrypted servers.
- I advise sticking to well-known, reliable sites and taking extra precautions to ensure your security.
- “It’s a web browser. Use it like one. It’s that simple,” says Muffett.
- ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users.
- The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers.
- Websites and data on the dark web do typically require a special tool to access.
Report It To The Authorities (if It’s Safe To Do So)
In fact, create new throwaway accounts and documents if possible. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. Avoid using payment methods that can easily expose your identity. Today, many organizations exist that are created only to handle these reports anonymously and effectively. They know how to process the information and get it to the correct law enforcement agencies internationally.
Disadvantages Of The Tor Browser
There are huge numbers of such pages, and most exist for mundane reasons. Thus, sites on the Dark Web can be visited by anyone, but it is very difficult to work out who is behind the sites. And it can be dangerous if you slip up and your identity is discovered. It is a relatively new provider but offers better features than most established VPNs.
Tor-over-VPN Vs VPN-over-Tor: The Right Order

To reduce the risk of these threats, it’s highly recommended to disable JavaScript when browsing dark web sites. That doesn’t mean it’s impossible to track users on the dark web. If you log into personal accounts on the dark web or visit websites with tracking scripts, then your activity may be tracked.
How Do I Access The Dark Web Safely Using Tor Browser?
Just like Google, the dark web has some search engines present on it. Though they have their limitations, most of the time you’ll see irrelevant or spammy links for your search results. You can choose the best darknet (.onion) website that suits you and start surfing.
- Choosing Tor over standard browsers is crucial for dark web navigation due to its unique privacy features.
- Proton VPN makes it easy to safely gain access to the dark web by connecting users to the Tor Network in a single click.
- These markets operate similarly to physical drug markets but are hidden from law enforcement through the use of the Tor network.
- There are multiple search engines on the dark web that can help you find what you’re looking for.
- Digital surveillance and cybercrime continue to rise, underscoring the need for disciplined cybersecurity habits.
Essential Tools For Secure Dark Web Access
There are different levels of security in the browser that are worth considering. To review security settings, click on the onion logo in the top left and select “Security Settings”, which will bring up a slider offering a choice of the default of standard, or safer and safest. In “safer” mode, JavaScript is disabled on HTTP sites, some fonts are disabled, and all audio and video won’t run automatically, you’ll have to click to play.
During that period, on top of the risk of accidental disclosure and theft, governments and the police could ask ISPs to share data. Many turn to the dark to grab such medications with its private and secure networks. Some common pain relievers and sleeping pills available in the EU are illegal in various Middle East and Asia countries. The story hints at why taking dark web safety measures is essential, even if you are jumping into the dark side of the internet only because of some curiosity. Interestingly, darknet sites also offer stolen documents and passports from around the globe.
Proton VPN has decent connection speeds and has tools for giving long-distance connections a bump. Its VPN Accelerator distributes the CPU load between multiple processes in OpenVPN, and modifies the servers’ Linux stacks to shorten the normal packet processing path. All Surfshark servers are RAM-only and support the WireGuard, IKEv2, and OpenVPN protocols. The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a SHA512 authentication hash and 2048-bit DHE-RSA key exchange. While NordVPN is undoubtedly a great service, it’s not without fault.



