Dark web websites are hidden under layers of encryption that cloak user activity, which can be a boon to whistleblowers, activists, and others who don’t want anyone tracking their activity. Finding websites on the Dark Web typically involves using specific directories, such as The Hidden Wiki, or search engines like DuckDuckGo, Torch, and NotEvil. These resources can guide you to various legal .onion sites, ranging from forums and news outlets to more specialized services. Tor’s anonymity has spurred many malicious actors to host dangerous sites on the network, including scams, phishing links, malware, and illegal content.
It’s Pretty Good
Unfortunately, some oppressive regimes have figured out a way to block Tor traffic. Unfortunately, the dark web is also where underground marketplaces flourish, selling drugs, weapons, stolen IDs and credit cards, and other ill-gotten goods. It is also used to facilitate human trafficking, money laundering, and worse.
IPhone Or IPad
A regular dark web browser will only encrypt your browser traffic; Orbot goes further and encrypts all data in and out of your phone. It is a mobile application that uses your Android or iOS device’s VPN mode to route all traffic through the Tor network. Broadly speaking, any internet browser can access the dark web with a few modifications. Brave is easier to set up, though, and is already more privacy-oriented than most browsers.
Dark Web Search Engine
While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store. So, once you’ve activated your VPN and your privacy is secured, it’s time to visit Tor’s official download page. Make sure that when you download the Tor file, it’s from their official website. It might sound weird that Google doesn’t index these pages, but it does carry some logical sense.
For totally hiding all of your online antics, you’ll want to also use a VPN. Just remember, both the Tor Browser and VPNs will slow things down, so you’ll likely not be happy with streaming through the Tor Browser. Live OS options that can be run on nearly any computer by simply popping a USB stick in and booting from it include Subgraph OS, Freepto, and Tails. If you find that Tor is restricted in your current location, you can use a bridge. A bridge creates an obfuscated relay on the Tor network that is not listed in the main directory. That means that even if an ISP is monitoring all of the known Tor relays, they may not be able to block all of the obfuscated bridges.
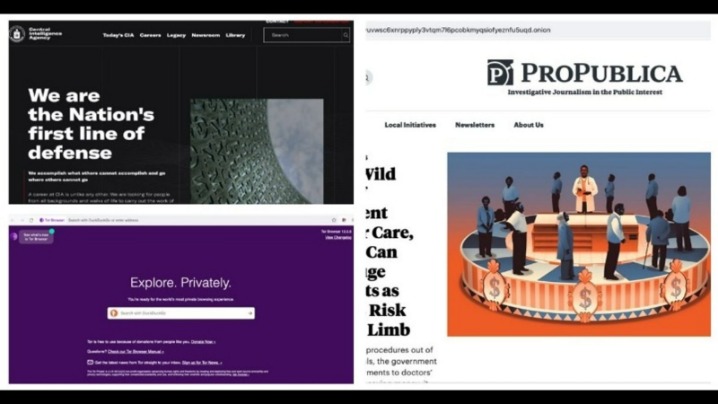
Does The CIA Have An Onion Site?
On average, the marketplace consists of more than 11,000 items and 1000 vendors. Besides this, it supports wallet-less transactions and accepts payments through Bitcoins, Litecoin, Monero, and Zcash. However, you must wait some time to reassess this marketplace because it’s been shut down. It issued a press release revealing that, from December 2021, the website won’t be functional anymore. Cypher marketplace has been on the list of the best dark web shops for a while and deals with the business of a variety of products and services.
ProtonMail is an email service that uses end-to-end encryption, making your email accessible to you and only you. The service retains no copies of any data that passes through a ProtonMail account. Although ProtonMail also exists on the clear web, accessing it via Tor provides an extra layer of privacy if you don’t want to leave a trace of you even using ProtonMail. Although profiting from pirated copyrighted material is unethical and illegal, there are some exceptions to using copyrighted material, such as a “private study” provision under UK law.

Ways Small To Midsize Businesses Can Stay Safe In The Cloud
It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites. It offers top-of-the-line security and fast speeds for a smooth browsing experience on the dark web. You risk being targeted for attacks if you explore the dark web without protection.
It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last. Simply accessing the dark web and using the Tor browser may already raise government suspicion. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
Top VPN Deals
Believe it or not, some dark web marketplaces have pretty advanced systems for building trust. Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews. In 2019, there were approximately 8,400 active sites on the dark web, selling thousands of products and services daily.
- Basically, if a Tor IP leak occurs before you connect to the VPN, your real IP address will be exposed.
- The best part is that with Orbot, you can block or unblock specific apps.
- These browsers offer the best security and privacy for browsing the dark web on mobile devices.
- This type of government surveillance applies mostly to countries with environments that are hostile to free speech.
- You don’t need special tools or a special browser like you need to access the dark web (more about that later).
Balancing The Benefits And Risks

If you want to access the Tor network on your iPhone or iPad, you can use the Onion Browser app. The mobile app uses DuckDuckGo as its default search engine and is supported by the Orbit framework to provide secure access to the Tor network. VPNs are also used for accessing geo-locked content hosted by streaming services.
Practical Tips For Minimizing Risks
Site operators can also submit their own .onion sites for indexing. The other 90-95%—the Deep Web—is basically all the content not indexed by search engines. The Dark Web, by turn, is a fractional part of the larger Deep Web, and requires special browsers to view and navigate. If you want to access an .onion site, it’s only possible through the use of a specialized browser known as Tor.
This .onion link makes it impossible for hackers to impersonate your profile. Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public. Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies. This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. Unfortunately, it requires you to have an invitation code to create an account. This means you have to know someone who is already using the platform.
Pixel Privacy believes in digital privacy and does not believe in using it for heinous and/or illegal activities, and so the focus of this article will be on legal activities. Please send us in detail your device model, iOS version and steps you follow that this issue happens to you by emailing us at [email protected]. In addition, it has an automatic kill switch (Network Lock) that stops traffic if the VPN connection fails.



