
This makes it even harder for third parties to see your email traffic. Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. Facebook’s dark web version allows users to access the site where it is banned or restricted. Although the social application is known for collecting data on its platform, it does not like sharing the information with others. You can also use it within the dark web, as it has .onion links. It will offer you an additional layer of encryption to access the deep parts of the internet.
Actually let me explain, everywhere the dark web (not deep web) is described as some notorious place that has all these absolutely mind-blowingly illegal things. Tor has an in-build slider which lets you adjust the level of security. This means that the JavaScript will be disabled by default on every website and some symbols and images will not be displayed. As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman. It’s also used by journalists, advocacy group members, and political refugees in hiding. Reuters, Fox, NBC, CNN – all of them keep open dark web channels to receive anonymous tips from whistleblowers.

How Can I Increase Security While Using Tor?
These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection.
Exiting Safely

Such data includes medical records, financial information, research papers, private forums and networks, and other content. The top layer is referred to as the clear or “surface web,” which is what you’re accessing while reading this article. The clear web is made up of websites that you can get to via a search engine like Ecosia or Google. Your clear web browser activity can be logged and tracked by advertisers, governments, and your ISP if you’re not using a VPN. This will help you to remain anonymous and secure at all Tor entry and exit nodes.
The VPN connection will route your online activity through a different server, masking your activity from your internet service provider. If you don’t have or use a VPN already, we have roundups of the best VPNs overall and the best free VPNs if you’re on a budget. Even in an era of increased online surveillance, the average person on the internet likely has too much to lose to bet on their safety for curiosity’s sake. Heck, I’m one of PCMag’s resident security experts, and I’m not playing around on the dark web just because I know how to. That’s why I’m not going to provide links or detailed instructions for accessing the internet’s shadier side. Ruheni Mathenge specializes in writing long-form content dedicated to helping individuals and businesses navigate and understand the constantly evolving online security and web freedom worlds.
Step 3: Install And Launch Tor
- Users leverage these platforms to organize protests, whistleblow, share survival guides, or share files P2P.
- This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs.
- Like I2P, Freenet is a self-contained network within the network that can’t be used to access sites on the public web.
- Over the years, I’ve been hearing about kids from my school accessing the dark web, some kind of weird “I’m a hacker” circlejerk.
- Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity.
Plus, in our day in age, getting to know computers a bit more ain’t a bad idea in my opinion. I no longer believe that people are paranoid because of having concerns like these. Information being sold is a real problem and it is now becoming a fear of mine. Over the years, I’ve been hearing about kids from my school accessing the dark web, some kind of weird “I’m a hacker” circlejerk. I’ve always been kinda curious myself about how to access it, how to navigate around it, and how to keep yourself safe when browsing. Btw, any ideas are welcome, don’t have to be an absolutely working concept.
What Is The Dark Web? Here’s How To Access It Safely (and What You’ll Find)
I possess a keen interest in exploring and understanding the intricacies of malware, Advanced Persistent Threats (APTs), and various cybersecurity challenges. My dedication to continuous learning fuels my passion for delving into the complexities of the cyber world. And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics. Great life advice, but it’s even more valuable where the darknet is concerned.
The dark web is used by journalists, whistleblowers, and political activists who need the protections that it offers. Anything you need to do that has to be off the books to some extent, for noble or ignoble reasons, can be done on the dark web. Accessing the dark web is easier than you might think, but it comes with risks. Only about 4% of the internet is visible to everyone, leaving the other 96% in the deep web. The dark web hosts a mix of legal and illegal content, with activities like pornography, drug trade, and weapon trafficking taking up a significant chunk.
Roundup – Best VPNs For The Dark Web
However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. Now that you’ve completed the download, it’s time to install the Tor browser on your device. (The installation instructions that follow are for the macOS platform, I’ll mention where it’s different for Windows.) Simply double-click the downloaded file in your download folder.
Beginners Guide To Using The Deepweb/TOR
- As the most widely used anonymity network, Tor routes your internet traffic through a series of volunteer-run servers (relays) around the world.
- This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity.
- Other sites explicitly block search engines from identifying them.
- Make sure that when you download the Tor file, it’s from their official website.
- Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito.
ActiveX and Java frameworks are susceptible to being exploited by hackers. Since you are navigating in uncharted territories with all the myriad threats today, you’ll have to disable them in your network settings to stay safe. Many dark web sites offer malware as a tool for cyberattacks. Since malware lingers across the dark web, your device can easily become infected, even if you are an unsuspecting user.
The threat can extend to your entire network of devices connected to the internet. If the above average Joe’s explanation isn’t enough for you, below are some legitimate reasons to use the Dark Web in a bit more detail. Activists and government critics prefer to remain anonymous, fearing repercussions if their identities are revealed.
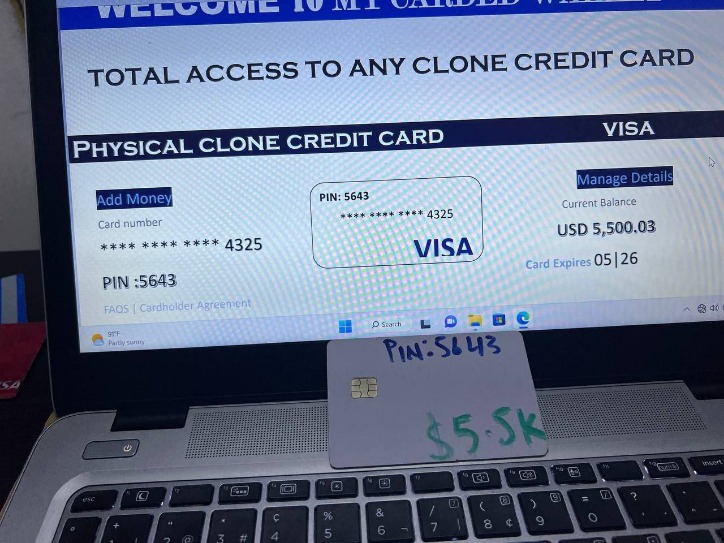
But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web. Silk Road became one of the most famous online black markets on the dark web for illegally selling drugs. So, that means that the number of pages increased by over 100 trillion in just over three years. Hypothetically speaking, Google may be aware of well over 200 trillion individual pages (these are obviously NOT all indexed in the search engine).
Words Of Caution When Using Dark Web Sites
However, note that the site only uses non-sensitive and public data for the metrics. The Tor Metrics is a good place to get more information about the Tor project. It collects data from the public Tor network and archives historical data of the Tor ecosystem. Since Hidden Wiki maintains all kinds of websites, ensure you don’t open something you don’t want to see. For example, it has a reputation for hosting pedophile sites.

Disable Java And ActiveX In Your Network Settings
No standard web browsers can be used to access dark web content. Journalists and whistleblowers, including Edward Snowden himself, often use the dark web and Tor to exchange sensitive information. For instance, the Ashley Madison data dump was posted to a site only accessible to Tor users.



