If used properly, the Tor browser allows surfers to stay anonymous and go to “members only” forums where they can use untraceable cryptocurrencies for their purchases. A reference to how Tor works; sending encrypted traffic through layers of relays around the globe as it hides content, the sender, and their location. Users need a special browser with added software to access the tor dark web in the first place. In order to understand the dark web properly, you need to understand that the internet is a huge and sometimes disorganized place.
BBC Tor Mirror
From information security threats like identity theft and malware to scams and surveillance, navigating the dark web without caution can lead to real dangers. So, is the dark web a lawless underworld or a misunderstood frontier for privacy and free expression? If your work or lifestyle requires you to use the dark web, however, there are ways to protect yourself. Just as you need the right tools to access the dark web, you also need the right protections to be able to stay safe on it. Before you go exploring the dark web, it’s crucial to recognize that it is much more dangerous than the surface web — and not just because of all the illegal activity happening on the dark web.
Everything You Need To Know About Dark Web Scanning
The most interesting thing about NordVPN is its built-in Onion over VPN feature. It encrypts your traffic at the entry node and changes your IP address. This means you will get a VPN’s security and enjoy the anonymity of the Tor network simultaneously. NordVPN is one of the best VPNs to combine with the Tor browser whenever you want to surf dark sites.
How Many Dark Web Sites Are There?
And given recent revelations about US- and UK government snooping on web use, you may feel it is sensible to take your communication on to the Dark Web. You can also read our in-depth guide to using Tor if you want to know more about using the web anonymously and sending messages securely. Put simply, there’s a lot more secrecy than the already secret act of using Tor to visit a website on the open internet – for both parties. When you purchase through links in our articles, we may earn a small commission. Install Avast SecureLine VPN for iOS to protect your privacy and keep your data from falling into the wrong hands. Install Avast SecureLine VPN for Android to protect your privacy and keep your data from falling into the wrong hands.
The visitor has to use the same encryption tool as the site and – crucially – know where to find the site, in order to type in the URL and visit. Almost all sites on the so-called Dark Web hide their identity using the Tor encryption tool. You can use Tor to spoof your location so it appears you’re in a different country to where you’re really located, just like when you use a VPN service.
Dark Web Myths Vs Reality
Get Avast BreachGuard for Mac to protect your privacy and keep your personal data from falling into the wrong hands. Get Avast BreachGuard for PC to protect your privacy and keep your personal data from falling into the wrong hands. While some reports of dark web murder-to-order are overblown, it is possible to commission acts of cybercrime on the dark web. These range from phishing campaigns to DDoS (distributed denial of service) attacks, which can take down entire servers and websites. Removing your sensitive personal information from the dark web once it has been exposed is virtually impossible.
- Next, select a dark web search engine like DuckDuckGo that can help you find dark web websites that cannot be indexed by traditional surface web search engines, such as Google or Bing.
- Global agencies use powerful tools to monitor, infiltrate, and bait users.
- Like the Deep Web, Dark Web also cannot be accessed using conventional search engines.
- However, certain activities, like purchasing illegal items or engaging in prohibited activities, are punishable by law.
What Is The Dark Web? Understanding Its Risks, Uses, And Mysteries
Even without the code, you can visit the security section to get tips on improving your daily life privacy. SecureDrop is a dark web link that allows whistleblowers on the dark web to communicate and share information with journalists safely and without being tracked. It aims to advance research on terminal illnesses like cancer with access to unbiased scientific publications.

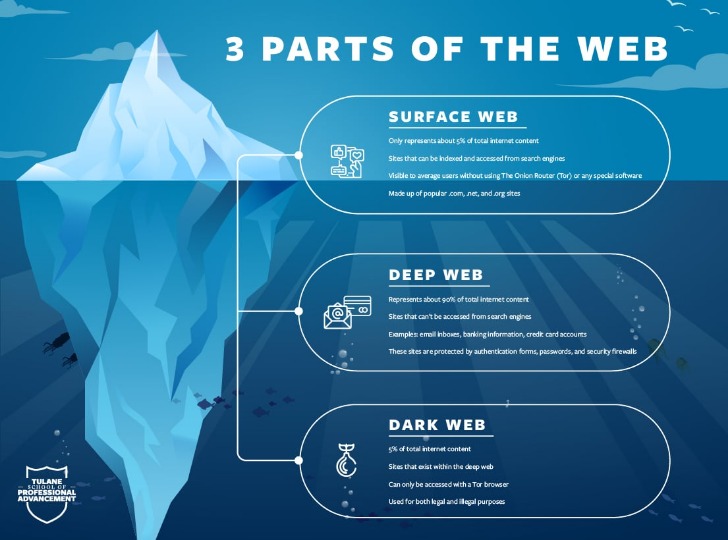
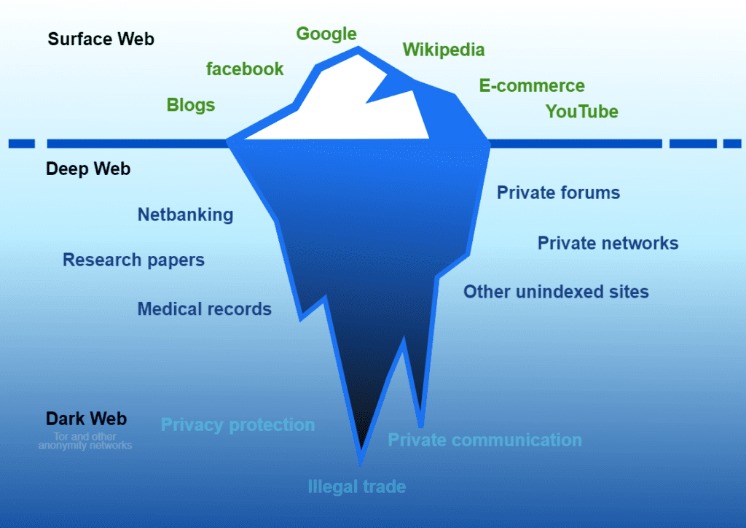
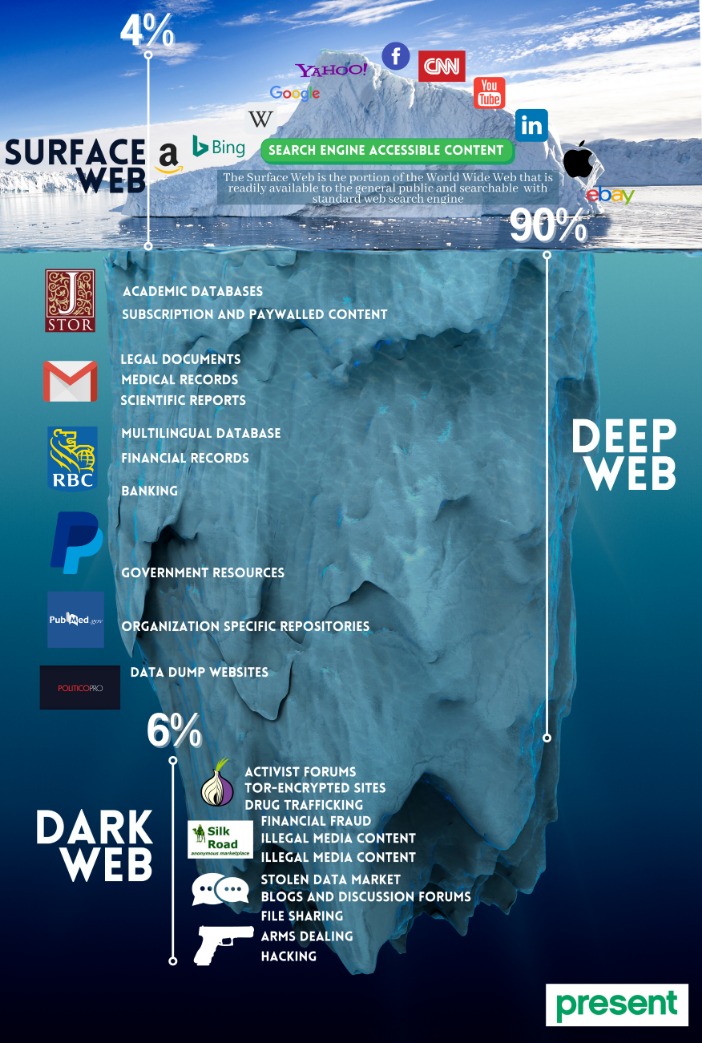
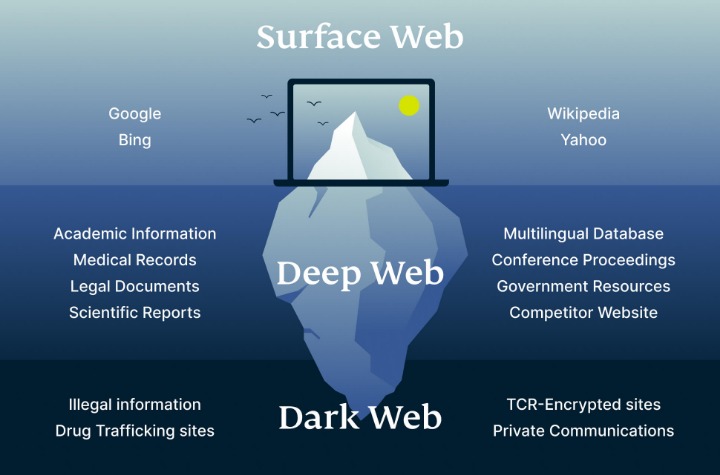
By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations. If you’ve ever checked your medical results online through a portal that required a login, you were navigating the deep web. It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. Cybersecurity has to also cover everything physically on your computer too—which law enforcement or government authorities might have the right to seize if they come calling.
Dark Web Vs Deep Web Vs Surface Web
These services include multiple incarnations of TorBook (named after the Tor network), Blackbook, TapIIN, and many others. The difficulty is maintaining a dark web social media network presence that remains anonymous. Furthermore, there is the ever-present issue that the site might disappear overnight, leaving you locked out of your account permanently. For example, you can find Bitcoin tumbling services which attempt to sever the link between Bitcoin’s digital transaction history and the user, further boosting anonymity. There are also countless cryptocurrency gambling portals, which may scam you, and just outright scams offering to double or triple your Bitcoin holdings for nothing. The strength of the encryption and the difficulty of tracking online activity on the dark web make it the perfect online location for all manner of malicious and dangerous activities.
The Role Of Forest VPN

It’s a part of the internet that’s less regulated and more shadowy, for better and for worse. Going to dark websites is not against the law, but doing unlawful things or viewing illicit content is. Anyone accessing the dark web via insecure means, such as without a virtual private network (VPN) or the Tor browser, should exercise extreme caution.
Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet. Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only. Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. The dark web is dangerous due to the presence of scams, malware, and illegal material. The use of tight security measures, dedicated hardware, and awareness are required to prevent these threats. SentinelOne’s Singularity Endpoint continuously monitors system activities, file changes, and other critical processes to protect against malware and dark web security threats.
How To Access The Dark Web Safely And Securely
Similarly, the dark web serves as a haven for privacy-conscious users who wish to keep their online activities shielded from pervasive tracking and data collection. Law enforcement agencies and cyber threat intelligence specialists also use the dark web. Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. RiseUp is a top dark web website that offers secure email services and a chat option.



