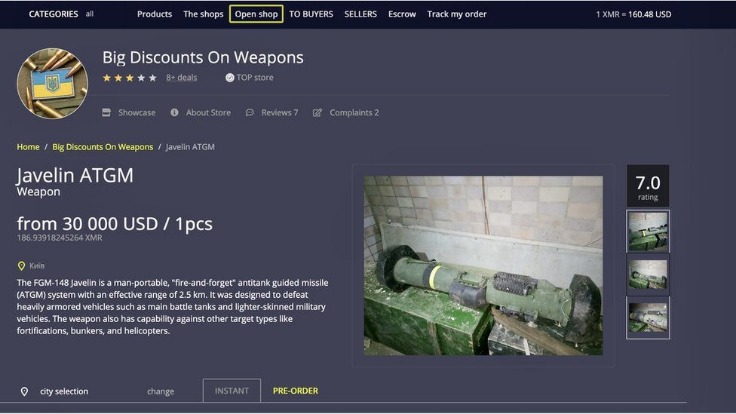
Besides ever increasing hosting costs, the site will have to contend with authorities, attacks from hackers, and the occasional disgruntled market administrator. Most dark web marketplaces use cryptocurrencies like Bitcoin for transactions to help maintain anonymity. Once a buyer makes a payment, it’s usually held in escrow until they receive what they bought. Dark web forums typically look like run-of-the-mill message boards.
By integrating these tools with secure browsers, users can confidently navigate the dark web while maximizing security, anonymity, and digital privacy in 2025. Protecting your digital identity is crucial when navigating the dark web. Password managers and anonymous email services prevent unauthorized access and ensure private communications. Freenet operates uniquely, functioning as a decentralized, peer-to-peer network rather than a traditional browser.
Can I Showcase My Torzon Mirror Projects On Torzon Url?
In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network. At the time, the internet was still young, and tracking people was easy while staying anonymous was not. The Tor network allowed safe communication channels for political dissidents and American intelligence operatives around the world. Fraud and scams run rampant on the dark web, including offers too good to be true and fake services requiring upfront payment.
Let’s look at two popular browsers you can use to access the dark web on desktop computers and laptops. Take a look at your Tor Browser settings before you start your first dark web browsing session. It has a range of settings you can configure to help with security and privacy. Disabling JavaScript, ActiveX, and Flash plugins, for example, will help to strengthen your privacy, though this may also cause some sites to run poorly. It will route your traffic through multiple servers instead of one, making tracking your data and activities even harder. In addition, it has an automatic kill switch (Network Lock) that stops traffic if the VPN connection fails.
How To Access The Dark Web Using Tor Browser (2025 Guide For Beginners)
Today, Tor Browser software is built on top of Mozilla Firefox, providing a familiar interface for users. Its popularity is constantly increasing, especially among those who need anonymous access to the internet, both for legitimate and illegitimate purposes. Tor was first introduced in 2002 as a project developed by the United States Naval Research Laboratory (US Naval Research Laboratory). The original goal was to create a secure communication tool for military intelligence.

Examples Of Legal And Useful Dark Web Content
A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web. Like I2P, Freenet is a self-contained network within the network that can’t be used to access sites on the public web. It can only be used to access the content uploaded to the Freenet, which is a peer-to-peer distributed data store. Once you upload something, it stays there indefinitely even if you stop using Freenet, so long as it is popular.
Official Security Advisories And Documentation
- This could include a massive concentration of marketplaces, forums, communication channels and other hidden services, all accessible via anonymous networks such as Tor or I2P.
- Also, your data is more likely on the deep internet in one way or the other.
- It also introduced a bug bounty program, hired a cybersecurity consulting firm to test its infrastructure, and then carried out a third-party security audit.
- Our mission is to simplify navigation in the complex and evolving world of the darknet.
It is a good place to get help and ask questions about the dark web when you are a total noob. Anybody wanting to connect to the dark web on an iPhone or iPad is advised that there is no official Tor app at the moment. Instead, Tor Project recommends iOS users to connect using the iOS Onion Browser app. It is vital that you only ever download the Tor browser from the official Tor website because there are malicious versions circulating online that contain malware.
This hides your Tor usage from local networks, masks direct Tor connections, protects against network-level surveillance, and reduces the risk of being flagged for accessing privacy tools. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for. You’re also open to threats like end-to-end correlation attacks, so while Tor is a lot more secure and private, it’s by no means completely safe.
What Is APKPure And Is It Safe To Use On Android?
As with the Imperial Library, you should be aware of copyright infringement. ZeroBin is a wonderful way to share the content you get from dark web resources. It is a reliable messaging tool where you copy/paste a text or image and send it to your addressee. In most cases, whistleblowers have sensitive information about the government or a company. They can be easily traced and even prosecuted if they share the information on the surface web.
However, over time, Tor evolved into an open-source project that can be accessed by anyone, including activists, journalists, and the general public who want to maintain their privacy online. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals. Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem.
Unlock Live Translate & Live Caption Feature In Google Chrome: An Easy Way To Enjoy Global Content
The dark web has several convenient uses, which are not all basic. People who live under a government that deeply supervises or censors internet traffic eventually get attracted to the dark web. Such people can be opposition figures from dictatorship-led countries, politically oppressed guys, whistleblowers, or journalists. The dark web is rife with cybercriminals who offer their services either as individuals or as part of a group. These groups include Mazafaka, Trojanforge, hack forum, xDedic, and dark0de. Some of these cybercriminals are known to track and blackmail pedophiles.
Subscribe To Our Blog For More News And Updates!
Your Internet service provider, or ISP, is your gateway to the Internet. While a website can’t identify you or an ISP can’t decrypt your internet traffic; still, they can still see you using Tor, which can draw some unwanted attention and raise suspicions. Many countries, such as Qatar, China, Cuba, Russia, and Turkey, censor internet content promoting political dissent. The Darknet offers a place of free expression where not even a chunk of these limitations exists. Many turn to the dark to grab such medications with its private and secure networks.
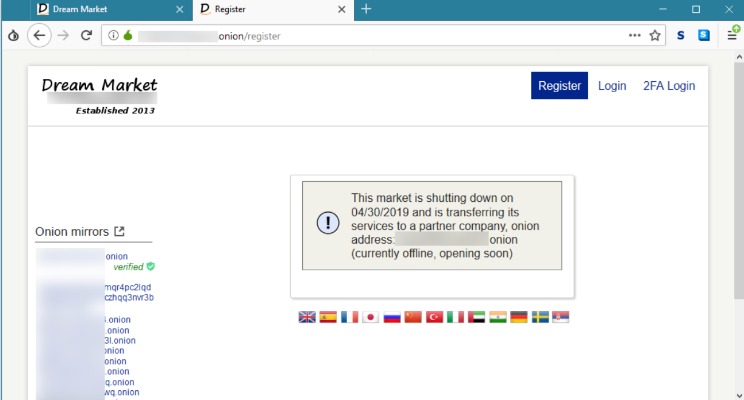
The Most Popular Dark Web Search Engines
Also, you must log in or have a specific IP address or URL to access the deep web content. Tails always starts with a clean slate and any evidence of the activities you engage in while using Tails disappears when you shut down Tails. This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down.
How To Access The Dark Web On Android
Tor is both a type of connection – with the extended relays – and a browser. With your device running a Tor browser, you can go to Tor-specific sites – those with an .onion suffix — or also visit the usual sites on the open web. The connection between Tor’s dark net and the regular internet is bridged via an ‘exit node’. Any internet traffic leaving the exit node is no longer part of Tor’s dark web. For maximum security users should only access sites with the .onion suffix via the browser. TorLinks serves as a backup or secondary directory site to the popular Hidden Wiki.
Crimes range from data theft and selling illegal goods for cryptocurrencies to human trafficking and more severe offenses. There are also privacy and anonymous browsers, which are designed to keep you safe on the regular ‘open’ web. For example, the Epic browser is programmed to always run in private mode, so it doesn’t store data about which sites you visit. It is based on Chromium, the open-source of Google chrome but the developers claim to have removed all Google tracking software and that the browser stops other companies from tracing you too. Unlike the open web, these sites aren’t really worried about being found by on-page SEO tools like web crawlers.



