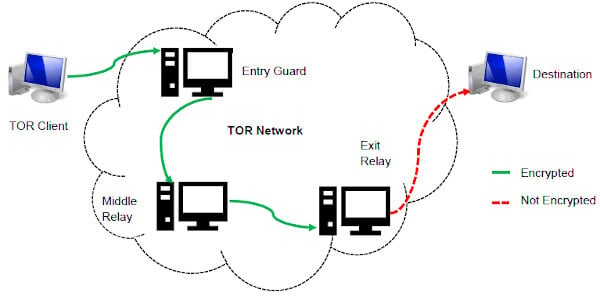
It will normally take a while to connect because Tor — unlike other browsers — will route your traffic through different nodes. You should also keep in mind that overall speeds will likely be impacted; for example, a page might take a few seconds longer to load than what you are used to. To access a dark web address, you must use a VPN and a suitable browser (it should be Tor).
Security Blogs
Whited’s rule of thumb is to use the Tor Browser instead of Private Browsing Mode or Incognito Mode. “Contrary to what most people think, these modes do not actually protect your privacy,” she says. As hoped, the Tor anonymous network grew in popularity among computer enthusiasts, privacy advocates, journalists, dissidents under repressive governments, and others desirous of strict secrecy. At the same time, Tor became an effective shield for the illicit sale of heavily controlled goods, such as guns and drugs. The Tor network also gave hackers, terrorists, and distributors of illegal pornography a secure method of communication. The term dark web first appeared in print in a 2009 newspaper article describing these criminal applications.
How It Works: VPN Over Tor
Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers. Well, now it’s time to fire up Tails and do a little bit of tinkering. Chill, because nobody will ever find a record of you ever fiddling around the darknet.

This contrasts greatly with Big Tech companies like Google, which exploits your personal data for profit. As mentioned above, Google collects a wide variety of personal data. This presents both privacy and security risks, as leaked data is a major problem. Even data which is not used for ads, such as Gmail data, is still collected and could therefore be leaked in a breach or government data request. We founded Proton in Switzerland in 2014 specifically to resist mass surveillance and abuse of personal data by US tech companies.

How To Download And Use Tor
If you want to be extra safe, routing your connection through a VPN and then accessing the dark web using the Tor browser provides more security than Tor alone. You can also use the Tails operating system to further protect yourself. If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough. If you’re trying to hide from an oppressive government or want to be a whistle-blower for something illegal, take as many steps as you can to be safe.
And if you’re a freelancer or operating a business, Proton has multiple plans to keep your business data secure. We offer a suite of end-to-end encrypted business solutions to protect your entire workspace, however big or small your business. Based in Switzerland, Proton is protected by some of the world’s strongest privacy laws, which are designed to safeguard your data from unauthorized access, including from governments. At Proton, giving you the ability to easily protect your privacy and most sensitive, valuable information is central to what we do.
Avoid Sharing Personal Information
Blockchain even has an HTTPS security certificate for even better protection. Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.
What Is The Dark Web? How To Access It And What You’ll Find

This means you can visit the site anonymously using the Onion browser, especially if you live under an oppressive regime. This article lists some of the best dark web websites you can visit securely. Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun.
First, Install A Reliable VPN
As a result, you can be exposed to different malware types, including botnets, ransomware, keyloggers, and phishing. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. It works by sending internet traffic through volunteer-operated nodes all over the world. This network of over 6,000 relays hides your location, thus protecting you from online surveillance and third-party tracking by your websites. Using the ProtonMail .onion site offers security and privacy advantages. Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection.

Navigating Ransomware Attacks While Proactively Managing Cyber Risks
In addition, even if the Tor node fails, your data won’t be exposed because the VPN’s encryption still holds up. As mentioned, we recommend using a safe provider like NordVPN, which also offers Onion Over VPN servers perfect for accessing the dark web safely. Individuals can access the dark web by installing specific, anonymous browsers, such as TOR.

Responsible use protects your privacy while staying within the law, so it’s a safe place to browse for real privacy reasons. Dark web forums are very similar to their clear web counterparts in almost every way, except for the content they discuss. Indeed, some began life on the clear web before migrating to the dark web to evade surveillance or censorship. Forums cover the breadth of criminal activity but these examples show there is a particularly thriving community of cybercriminals sharing information, tutorials, access, and exploits. Staying cautious is essential when interacting with content on the dark web, as illegal activities are prevalent. Users should refrain from clicking on unverified links and exercise discretion in revealing personal information.
By applying well-defined criteria, you can more confidently separate valuable platforms from malicious or untrustworthy ones. Also known as Not Evil, this dark web search engine offers access to a wide array of .onion content. You can enter .onion URLs directly into the Tor Browser’s address bar or visit directories like The Hidden Wiki to find popular sites on the dark web.
- There are a lot of misconceptions about it, but we’ll answer that question once and for all in this guide.
- Once you have those, there are several ways to tunnel through the dark web.
- Others may act in ways that are illegal for the protection and safety of others.
- Hackers sell access to email accounts, social media profiles, or other information that can be used for identity theft.
- Douglas was invited by the EFF to help host a livestream session in support of net neutrality.
Dark Web Search Engine
Illegal marketplaces are merely a small fraction of what’s actually there. Our editors thoroughly review and fact-check every article to ensure that our content meets the highest standards. If we have made an error or published misleading information, we will correct or clarify the article. If you see inaccuracies in our content, please report the mistake via this form.



