
Hijacking a PayPal account requires a different approach than stealing a credit card number. Instead of card numbers and CVVs, criminals steal usernames and passwords that they’ve gathered either through phishing or malware. They can then sell the account credentials to a buyer who can log in and drains the funds, or the vendor can transfer the requested amount of money from the victim’s account to the buyer’s account.
Stolen Credit Cards Hit Dark Web For Free
Here is a detailed description of how scammers steal information from the credit card dark web. To access the dark web, you will need to download and install the Tor browser. This will allow you to access websites that are only accessible through the Tor network. If you’re unable to block the fraudulent charges, there’s no guarantee they will be refunded or removed from your statement.
Credit Cards Skimmed And Used As Marketing Tool
It’s also the latest in a growing list of criminal marketplaces to have voluntarily retired in the last six months. Many other illegal darknet marketplaces have also shut down voluntarily over the winter for unknown reasons. Accessing this hidden part of the web requires specific tools and knowledge, including the use of anonymizing software like Tor, which allows users to navigate while remaining undetected. Privacy is a BBB®-accredited company with a dedicated customer support team. As a company handling sensitive payment data, Privacy complies with PCI-DSS protocols and exceeds additional industry security standards to ensure the safety of your data.
- They allow stolen data to be bought and sold without easily traceable monetary trails.
- A quick guide for developers to automate mergers and acquisitions reports with Python and AI.
- The dark web is a complex, multifaceted entity—both a repository of illicit opportunities and a mirror reflecting our society’s growing reliance on digital transactions.
- Telegram carding groups have become a significant threat in the cybercriminal community, with tens of thousands of members easily accessible through the chat application.
- Follow our recommendations to secure your information, such as notifying your bank and updating security settings on your accounts.
Telegram Carding Groups
Carding has long been a prevalent form of online crime—and it remains a serious threat. One such protection is the use of anti-fraud tools, such as F‑Secure Total, our complete online security solution. These tools offer consumers the most effective way to defend against carding attacks. By monitoring dark web markets, we often discover data breaches before they’re publicly reported.

To pull off these credit card scams, D2 and other fraudsters would sign onto sites on the dark web and simply pay a small fee—as little as $35 — for victims’ credit card information. Sometimes hackers will commit “card-present fraud” by breaching the point of the sale at a physical store. Or they’ll commit “card-not-present fraud,” by hacking a website and stealing the online card information that gets entered into the checkout page. Credit card details can be sold as digital items on the dark web, with the basics costing around $17.36. Physical cards, on the other hand, are cloned from stolen online details and can be used to withdraw cash from ATMs. A second major leak of cards relating to Indian banks has been detected by Group-IB, with over 1.3 million credit and debit card records being uploaded to the Joker’s Stash marketplace.

As Porn Sites Apply New Age Checks, Will Users Hand Over Personal ID?
Stolen financial info sold online gives scammers instant access to victims’ money. This makes it crucial to monitor accounts closely and use strong security measures. Dark web credit card fraud poses serious risks to consumers and businesses alike. Regularly monitoring your credit card statements can help you detect any suspicious activity, such as unauthorized transactions. Wizardshop.cc was established in 2022, and offers a wide range of leaked CVVs, database dumps and even RDPs. In the past 6 months, the site has increased the volume of cards sold, placing itself as one of the top sites selling credit cards today.
- In most cases, one has to find a proper vendor on a DNM and usually buy his service by paying an entrance fee ($20-100) using the vendor’s listing.
- It is crucial to understand that not everything on the Dark Web is unlawful.
- If you notice anything unusual, contact your credit card company immediately to report the issue.
- The financial sector in the Kingdom of Saudi Arabia is particularly attractive to cybercriminals due to the high value of financial data and the frequency of online transactions.
Multi-sig is called 2-of-3 escrow service because it needs 2 consents (signatures) to proceed. If there is a dispute, the market staff decides who will get currency and provides the second signature. In multi-sig, DNM staff is still a party settling the disputes, but it doesn’t hold money and eventually, it can’t steal the deposits. In most cases, one has to find a proper vendor on a DNM and usually buy his service by paying an entrance fee ($20-100) using the vendor’s listing. While this topic may seem distant for most people, understanding how these spaces operate is crucial.
This process allowed us to calculate a risk index to more directly compare how likely your card is to be available on the dark web by country. To minimize the risk of payment data exposure, only shop from reputable retailers, use digital payment methods or one-time private cards, and protect your accounts with two-factor authentication. Financial data can leak in many ways—through phishing attacks, data breaches at online services, or poor account security. Even in regions like the EU, where banks are legally required to implement strong customer authentication, criminals continue to find ways to bypass these safeguards. He said some fraudsters would go as far as setting up entire businesses using merchandise bought with stolen credit card information, like a guy who flipped refrigerators, beds, and mattresses. This involves adding daily listings of stolen credit card details to the site and periodically dumping large amounts of stolen credit card details at the same time.

Never Conduct Online Transactions On Public WiFi Networks
Get the latest updates on privacy, plus expert tips, and security guides to up your digital protection game. Making payments online is faster, safer, and easier with Privacy Virtual Cards because of the straightforward interface and multi-platform accessibility. The pausing/closing feature is especially useful if a specific Privacy Card has been exposed in a data breach or you want to block hidden/unwanted subscription charges. Keep in mind that you still need to reach out to the subscription provider if you’d like to cancel the service. Spyware and malware attacks are another common tactic used by scammers to steal data, and they are typically a result of phishing schemes. Credit card theft has become one of the most common types of fraud, with the U.S. projected to lose a staggering $165 billion in the coming 10 years due to card abuse.
Chase Security Center
Offer pros and cons are determined by our editorial team, based on independent research. The banks, lenders, and credit card companies are not responsible for any content posted on this site and do not endorse or guarantee any reviews. All information, including rates and fees, are accurate as of the date of publication and are updated as provided by our partners. NFC (Near Field Communication) fraud is a growing concern due to the increasing adoption of NFC technology in mobile payments, identity verification, and other contactless applications.
Dark Web Monitoring Tools

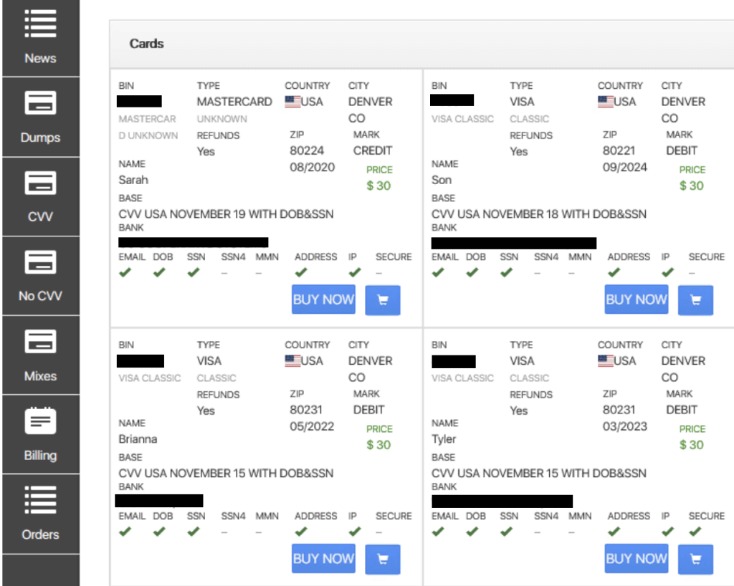
Payment information is stolen in a variety of ways before it ends up on the dark web. Many payment card numbers are stolen via data breaches; threat actors compromise payment sites, allowing them to stealth credit card numbers. Others might be stolen through phishing attacks on companies, stealing their customers’ payment information. Some credit card details are stolen using devices called skimmers, which are placed in card readers specifically to steal payment information.
Evaluating Seller Feedback And Ratings
Another tool, called King NFC, was previously marketed on the Dark Web as an alternative. Notably, the Telegram channels offering it are named X-NFC, which may create some confusion. The actors behind the tool provide technical support and guidance on how to use it. The dark web isn’t a single destination but a collection of anonymized networks where privacy is paramount.
Depending on the goal of a cybercriminal, they may prompt you to enter your login credentials or your credit card information. Lastly, remember that the traditional web offers countless legitimate ways to engage in online transactions and protect personal information. Explore trusted websites and platforms that prioritize cybersecurity, privacy, and legal compliance. It is important to note that engaging in transactions on the Dark Web carries significant risks, and using payment methods that cannot be traced back to the buyer does not guarantee complete anonymity. Despite the pseudonymous nature of cryptocurrencies, law enforcement agencies and cybersecurity experts have developed sophisticated techniques to trace these transactions.

The dark web serves as a thriving marketplace for stolen credit card information. Criminals buy and sell credit card data, exploiting it for various illegal activities. This underground economy poses significant risks to individuals and financial institutions alike.
When Torrez closed in December it was one of the largest English-language marketplaces in the world selling drugs, hacking tools, counterfeit cash and criminal services. Surfing on the dark web, communicating, or transferring private information is legal. However, buying credit card information from the dark web is illegal and leads to severe penalties from the government. Dumps have negligible value and risk, while the Fullz credit cards’ dark web value and, therefore, the risk is the highest.



