
Please note that all material provided here is aimed at promoting awareness, responsible research, and ethical use of information. Cyber threat intelligence (CTI) helps organizations predict, understand, and defend against cyber threats, enabling proactive protection and reducing the impact of attacks. In repressive regimes, darknets play a vital role in enabling free speech and access to uncensored information. Tools like Tor are used to bypass government-imposed firewalls and surveillance, ensuring open communication. The significance here is the preservation of civil liberties and the right to information.
Use A Dedicated Browsing Machine
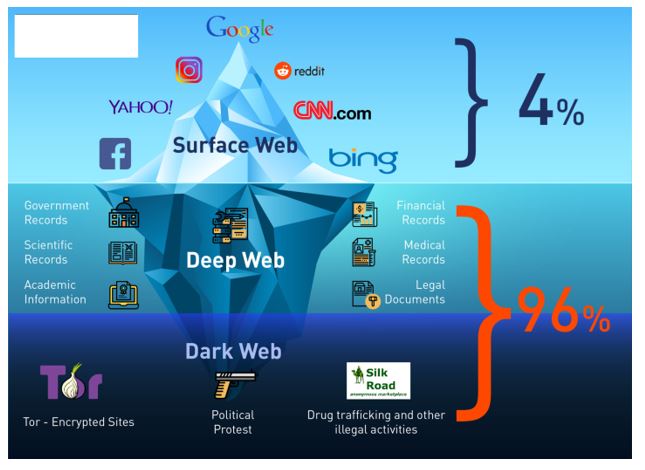
This includes accessing restricted channels and automating intelligence gathering to anticipate attacks targeting your organization, employees, and customers. Using software originally known as The Onion Router (think layers and layers of encryption), Tor secures traffic by routing it through a network of secure relays that anonymize traffic. These relays are run by volunteers around the world who donate their server bandwidth. If the surface web is the tip of the iceberg and the deep web is what’s below the water, then the dark web is what you’ll find deep in the blackest waters below. The darknet refers to the peer-to-peer network itself, whereas the dark web is the content that is served up on these networks. When you log in to internet banking, you’ve navigated to a specific location online, but one that’s not served up in Google results.
Ask: Does Titanium Set Off Metal Detectors At Airport Security?

Unlike traditional TLDs, servers using the onion TLD are more difficult to locate. This makes it more difficult for authorities to locate and take down these sites. Well, as long as you don’t visit sites with underaged models or that engage in human tracking or that sell drugs and other illegal items. Tor was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag. Tor was designed to protect American intelligence communications online.
What Do People Sell Or Exchange On Darknet Markets?

This high-security level makes the Tor browser fit for opening ‘onion’ links (dark web links), which use onion routing with several layers of encryption to protect your online traffic. The browser itself bounces web requests over three servers while encrypting the data before the request gets to the intended server. Most darknet market administrators are now tightening access controls.
Like Pierluigi Paganini indicated in his title, Digging the Deep Web explores the dark side of the web and expertly tells readers what they didn’t know about the internet’s underworld. Panganini’s vast cybersecurity experience helps provide a detailed explanation of the mysterious sections of the internet and the risks and benefits linked to accessing them. The book begins with the history of the dark web and moves to how to access dark web sites using special software like Tor browser, Freenet, or I2P. It guides you through downloading and setting up all three browsers. As stated earlier, neither of these connected content repository networks are illegal to access.
Is It Illegal To Use The Tor Browser?
It all starts with Tor, which keeps your identity under layers of encryption. The Tor browser conceals IP addresses and browsing activity by redirecting web traffic through a series of proxy servers operated by thousands of volunteers across the globe. This process, called onion routing, protects users from surveillance and tracking. The darknet, also known as the dark web, is a concealed section of the internet that’s inaccessible via standard search engines.

Safely Browse And Verify Onion Sites
There are many authoritarian governments across the globe, and people living under such regimes often need to anonymously communicate. In fact, it can often be much safer for people in such circumstances to use the Dark Web over a virtual private network (VPN). The Dark Web is used by cybercriminals to buy and sell illegal goods and services, coordinate attacks, distribute malware and phishing kits, and share other prebuilt exploits. But, perhaps a big surprise to anyone thinking the Dark Web is just for criminal activity, it can also be leveraged for legitimate purposes.
Bitcoin And Cryptocurrency
There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes. The release of Freenet in 2000 is considered by many as the start or founding of the dark web. University of Edinburgh student Ian Clarke created Freenet as a thesis project. Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito.
Scammers on darknet markets claim to offer legit tools or services, but instead provide you with malicious software that can infect your device. Many people use Tor to avoid surveillance by government agencies, ISPs, or other entities monitoring online activities. Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites.
- Abeerah is a passionate technology blogger and cybersecurity enthusiast.
- Immediately change your passwords, enable two-factor authentication, and notify your bank or credit card provider if the leaked information includes your financial data.
- Ensure you download the Tor Browser from the official website to avoid downloading malware, spyware, or other viruses to your device.
- Journalists, security professionals and everyday users alike rely on its anonymity tools to safeguard whistleblowers, protect sensitive research and evade censorship.
- This can often be for political reasons, but also because they may be involved in illegal activities, such as the ones listed above.
Award-winning journalist Evan Ratliff spent nearly five years piecing together the uncommon story. The Goodreads community has responded well to the riveting account of a crime boss with thousands of positive reviews, and it’s no secret why the book tops our list. It offers much information to help you learn how the dark web works. Interestingly, the man behind it pulled the strings from a laptop in Manila. A reclusive programmer turning criminal genius is certainly not your regular life cycle of a crime lord.

However, Cody’s book acknowledges that using the Tor network is not without its risks and challenges. It tells readers that using the network may expose them to malicious software and illegal websites. This book is one of many dark web books that tell beginners what the Tor browser is, how to navigate it, and how to use it to explore the dark web.
The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities. Of course, the promise of secrecy and unfiltered access might lure you in, but those same features are what make the environment so risky. Just like on the regular internet, phishing is a big problem on the dark web as well. Fraudsters create fake versions of popular darknet sites to trick users into entering login details or personal data. If you fall for it and log in, they immediately steal your credentials and either sell or use them for other scams. If you take a quick look through darknet marketplaces, you’ll instantly notice an overwhelming supply of pirated content.



