As mentioned before, your ISP and government institutions are not able to see what sites you visit on the Tor network, but they can probably see that you use Tor. Click on “Safest.” As you’ll see, JavaScript and a few other features will be automatically disabled on all sites. Be warned that this may cause some websites to not work properly. However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail. For more information, read more about the most secure email service providers in my other post. The majority of the users on the dark web use the Tor (The Onion Router) browser.
Download And Install The Tor Browser
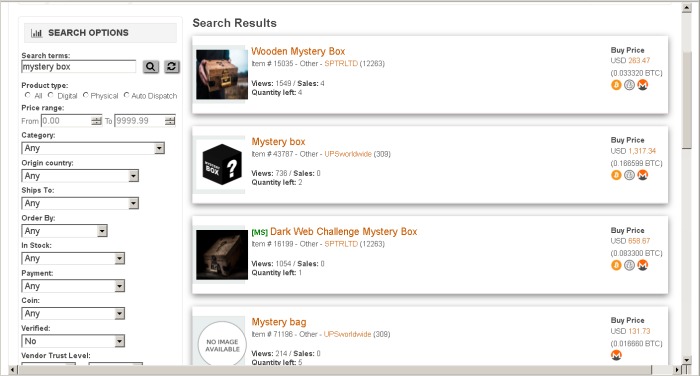
This is to address security concerns and to improve its presence. Today, Exodus Marketplace works from 3 different domains, two of which are its mirrors. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it. For instance, cybercriminals can buy credit card details with a $5,000 balance for just $110. It offers outstanding privacy features and is currently available at a discounted rate.
Taking part in any activity on any darknet market, both legal and illegal, will solely and exclusively be your own responsibility. In the internet’s darkest corners, a myriad of hidden websites cater to an array of needs and interests. From encrypted communication channels and hacking forums to illicit marketplaces, the dark web is a destination for millions of daily users. Read on to learn more about the five main types of darknet websites and what they contain. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. There are a lot of misconceptions about the dark web online and in popular media.
How To Hide IP Address In 2025 (A Comprehensive Guide)
This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know. The last thing you need to do is to start researching vendors and determine what marketplace is a possible vendor to buy the products from. From this point onwards, you can enjoy complete anonymity and security while being able to access “.onion” websites and other dark web browser domains. When you install a VPN, all of your activities on the dark web will be hidden from unwanted snoops from your ISP or the FBI. The VPN is a second layer of extra protection, on top of the protection that the Tor network already offers. The same anonymity that publishers enjoy on the dark web can be utilized by users who want to read the available information.
Malware Sales
Moreover, the reviews and ratings are more trustworthy and not controlled by the seller. You can simply search for “Darknet markets” on the search engine and it’ll get you hundreds of them. Darknet search engines are search engines which index darknet websites. You can use them exactly like you use Google, Bing, or any other clearnet search engine.
VPN Alternatives For Securing Remote Network Access
The ASAP is a moderate design marketplace on the dark web that offers helpful tools like mandatory PGP encryption and two-factor authentication for a safe browsing experience. Like other marketplaces, ASAP Market also requires you to register for an account. As these marketplaces keep changing, it is critical to stay on top of the main platforms on the dark web worth monitoring. Monitoring dark web markets is crucial, no matter if you are a business or individual, as you can then proactively identify and mitigate potential breaches and cyber threats. By following these steps, you enter the Dark Web with more confidence and preparedness.
Naval Research Laboratory in the mid-1990s and later released to the public. Tor, short for “The Onion Router,” routes internet traffic through a global network of volunteer-operated servers to anonymize a user’s online activity. This technology initially had noble intentions, aiming to protect activists, whistleblowers, and individuals in repressive regimes. However, it soon became a double-edged sword as malicious actors began to exploit its capabilities for illicit purposes. Darknets and dark markets have fueled the growth of cybercrime, provided a marketplace for cyber threats, and expanded the attack surface for malicious actors. Once installed, the browser functions like a regular web browser.
History Of Dark Web Marketplaces

Cybercriminals can rent or buy malware tools through darknet markets. This malware-as-a-service model allows less tech-savvy criminals to launch malware-driven cyberattacks without building the tools themselves. Law enforcement agencies monitor many dangerous markets, and even anonymous browsing isn’t foolproof. Just visiting these sites can attract attention from law enforcement, especially if you interact with known vendors or download suspicious content.
- It uses PGP encryption to protect sensitive data and messages, and accepts payments via Monera and Bitcoins to keep you anonymous on this marketplace.
- However, if someone were to pursue this, here are some safety strategies.
- It is a wallet-based shop, meaning you must first deposit bitcoins into your wallet before purchasing any goods and services.
- While this may all sound sophisticated, it is a financial crime and very risky.
- The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous.
Espionage And National Security Threats
No, black market websites operate illegally and pose high risks of scams, fraud, and law enforcement action. Some fake sellers take your crypto and never ship what you ordered, or phishing sites that look like real marketplaces but steal your login info. And then there’s malware—click the wrong link or download the wrong file, and your device could get infected. Others are looking for stolen data, hacking services, or even banned books and political content. For sellers, it’s often about making money while staying off the radar.
Key Features
If you want to share stuff with other community members then you can register here to join. Other sections of Cave Tor are news, guide, escrow, photos, blogs, Q&A, people and wiki links Tor. For proper loading of website, you need to enable JavaScript which is not advised at deep web. Here you can get Barbiturates, Benzos, Cannabis, Digital Goods, Dissociatives, Ecstasy, Opioids, Prescription, Psychedelics, RCs, Steroids, Stumulants, and Weight loss tablets.
If you get NordVPN, you can also use the Tor network whenever you want with its Onion over VPN servers. These are special servers from NordVPN that first hide your IP address and then route your traffic through the Tor network. We’ve compiled a detailed guide to help you explore the Top Darknet Markets. Discover the most trusted platforms like Anubis Market, and more, complete with their unique features and security measures. Anonymity starts with protecting your internet connection. Using a VPN (Virtual Private Network) in tandem with the Tor browser ensures an added layer of security by encrypting your traffic before it reaches the Tor network.
Is It Illegal To Browse The Dark Web?

Navigating dark web marketplace links can be risky; however, with the right tools, you can explore safely. Hydra is in Russian language so if you understand Russian consider this otherwise move to next. If you are looking for Russian darknet market then you can check out onion link for more information about Hydra. Green Road offers Cannabis, Depressants, Empathogens, Opiates, Pharmacy, Psychedelics, and Stimulants. If you are looking for dark web links that deal in drugs, you can consider this one as it is dedicated to only drugs.
Market Features
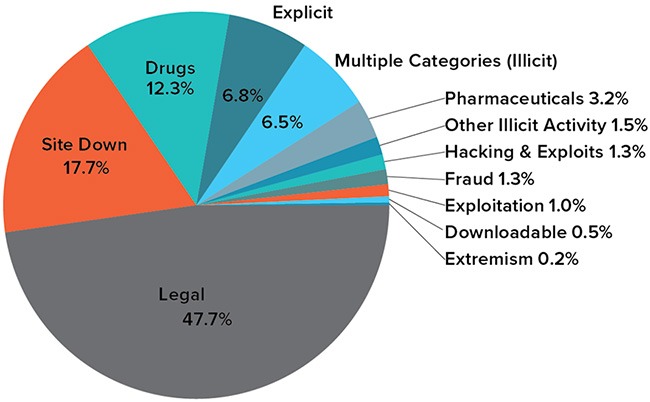
They’re tightening security and carefully screening anyone who wants to join. This vetting process helps keep the community “clean” from spies, law enforcement, or anyone who might pose a risk. According to a recent trend, the dark marketplaces faced a decline in revenue.
To reduce the risk of fraud, many dark markets offer escrow services. In this system, cryptocurrency is held by a trusted third party until the buyer receives the product or service as described. Once the buyer confirms satisfaction, the funds are released to the seller. From information security threats like identity theft and malware to scams and surveillance, navigating the dark web without caution can lead to real dangers. So, is the dark web a lawless underworld or a misunderstood frontier for privacy and free expression?



