It has a large network of secure servers, the ability to keep connections private, and apps that are rich in security features. It tends to conjure vague notions of bad people secretly doing bad things. But while it certainly is a place where illegal activities are facilitated, it can also be a force for good. A lot of the user data that gets stolen or leaked from big platforms ends up on the dark web, where users buy, sell, and exchange it among themselves.

What Is The Dark Web & How To Access It Safely In 2025
This infects a user’s device and essentially blocks them out of it until they pay a “ransom,” usually in the form of cryptocurrency (so it’s harder to track and recover). Users could accidentally fall victim to ransomware just by clicking the wrong link or downloading a file on the dark web. If you’re in the U.S., you can make use of helpful tools like ExpressVPN’s Identity Defender to inform you if and when any of your data ends up on the dark web. This will allow you to take action right away and reduce the risk of any further damage to your data or identity. Take a look at your Tor Browser settings before you start your first dark web browsing session.
Why Do People Use The Dark Web?
Law enforcement agencies around the world actively monitor the Dark Web for illegal activities, and many criminals have been caught and prosecuted as a result of their actions online. Even if users maintain their anonymity, they are not immune from detection. Some governments actively monitor dark web activity through various methods, like analyzing internet traffic patterns or using high-end surveillance software.
Stolen Data And Identity Theft
- Knowing if your information is on the dark web is a critical part of protecting yourself from threats.
- Hackers also use the Dark Web to exchange tools, tips, and techniques for breaching computer systems, creating a thriving ecosystem for cybercrime.
- As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman.
- We also prefer this method because of VPN’s all-encompassing security.
- Look for features like real-time alerting, coverage of multiple dark web forums and marketplaces, credential and data leak detection, and integration with your existing security stack.
- When venturing into the dark web, it is crucial to prioritize safety by educating oneself about potential risks and employing robust security measures to protect data and maintain privacy.
For one, the VPN can’t see your online activities because of VPN encryption. We also prefer this method because of VPN’s all-encompassing security. It encrypts your traffic right away, which is beneficial if you don’t want your ISP to see you’re using Tor. Some countries frown upon dark web usage, so it’s good to have your back covered by a reputable VPN service. The entry node encrypts your traffic and it bounces across several nodes in the Tor networks until it reaches the exit node.

It is important to note that while Dark Web search engines can help users find specific content, they do not guarantee the legitimacy or safety of the websites they index. Users should exercise caution and follow best practices for staying safe on the Dark Web. Search engines on the Dark Web function differently from those on the surface web.

Use A VPN Or Proxy For An Extra Layer Of Security

The Tor Browser is automatically configured to provide a certain level of privacy and security. Avoid installing additional browser extensions or plugins that could potentially compromise your anonymity or privacy. Once the Tor Browser has established a connection to the Tor network, a confirmation message or a green icon in the Tor Browser toolbar will indicate a successful connection. This signifies that your internet traffic is being routed through the Tor network. By following this step-by-step guide and exercising caution, you can access the Dark Web securely and explore this hidden part of the internet responsibly. If you have a legitimate or viable need to access the dark web, you’ll want to make sure you stay safe if you decide to use it.

Avoid Downloading Files From Untrusted Sources
Remember, navigating hidden services on the Dark Web requires a high level of caution and awareness. By following these guidelines, you can minimize the risks and have a safer experience. The history of the Dark Web is a fascinating journey that spans several decades. It originated from the early days of the internet and has evolved into a complex network of hidden websites and encrypted communication channels. Understanding the history of the Dark Web is crucial for comprehending its current state and the challenges it presents for cybersecurity.

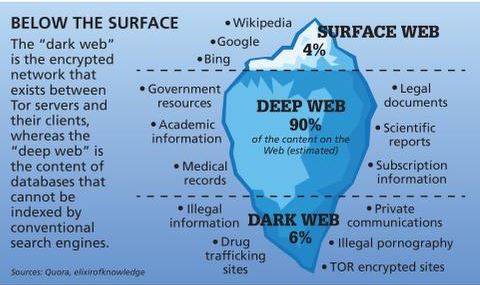
Any online activity can carry breadcrumbs to your identity if someone digs far enough. All commonly public-facing websites accessed via traditional browsers like Google Chrome, Internet Explorer, and Firefox are contained here. Websites are usually labeled with registry operators like “.com” and “.org” and can be easily located with popular search engines. This study examines the evolution of dark web usage, highlighting the surge in activity during the COVID-19 pandemic.
Minimize Or Rescale Your Tor Browsing Window
There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game. Services like Random Chat connects you with random people using the same service. Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web.
The VPN’s encryption will hide from your ISP the fact that you’re using Tor. Then there’s the less popular VPN over Tor, which is advised against by the official Tor Project. Only two VPN providers that we know of, AirVPN and BolehVPN, offer this service, although neither of these score highly for speeds. Internet traffic first passes through the Tor Network, and then through the VPN. This means the VPN provider doesn’t see your real IP address and the VPN protects you from those bad exit nodes. Again, we can’t emphasize enough that security and anonymity are paramount to those on dark websites.
Is Using The Dark Web Illegal?
The 2024 Global Threat Report unveils an alarming rise in covert activity and a cyber threat landscape dominated by stealth. Read about how adversaries continue to adapt despite advancements in detection technology. Microsoft Word is one of the best word processors around, allowing you to craft powerful documents with an intuitive interface. If you know how to use Microsoft Word, you’re typically working with large files that span multiple pages.
- Threat actors also exploit vulnerabilities in your systems and software to gain access to them.
- To access the Dark Web, you cannot simply type a URL into a standard browser.
- Ensure that you regularly backup your important data from devices that access the Dark Web.
- Additionally, educating yourself about common phishing tactics and how to identify and prevent them is crucial for staying safe online.
- As such, it’s important to be extremely careful when accessing the dark web, as you could inadvertently access a site containing, displaying, or linking to illicit content in some form.
- There are four nodes between your computer and the website you want to connect to.
The subreddit r/deepweb is a good starting point for asking more experienced users about how to search the dark web and deep web for the content you want. Lastly, The Hidden Wiki is a collection of dark web links — but the links may not work and can lead to dangerous websites. Dark web browsing is not as simple as regular web surfing, but there are some tools you can use to chart your journey. Dark web search engines and forums like Reddit can help you find reliable dark websites, and you’ll need to use a dark web browser to visit them.
These can include drugs, weapons, stolen data, and even hacking services. It is important to note, however, that not all activities on the dark web are illegal. Many individuals use it to communicate securely and anonymously or to access information that may be restricted or censored in their countries.
Their efforts help to identify, mitigate, and prevent a wide range of cyber-attacks, ultimately enhancing the overall cybersecurity posture of the organizations they serve. Fill out this form to request a meeting with our cybersecurity experts. Click on the download link for the appropriate version of the Tor Browser. The download should start automatically, but you may be prompted to save the file or choose a destination for the download. Select a location on your device where you will easily find the downloaded file. With many Tor-based sites being overtaken by police authorities across the globe, there is a clear danger of becoming government target for simply visiting a dark website.



