
So, if the website looks fishy, close the tab, and forget about it. Well, now it’s time to fire up Tails and do a little bit of tinkering. Note that the process can take anywhere from 5 to 30 minutes depending on your machine.

Where Can I Find Safe Onion Links?
To do so, enter a .onion URL and you’ll be taken to the dark web page being served at that address. H25.io is a premium directory in the Tor network, offering access to a diverse and meticulously curated list of onion sites. Our mission is to simplify navigation in the complex and evolving world of the darknet.
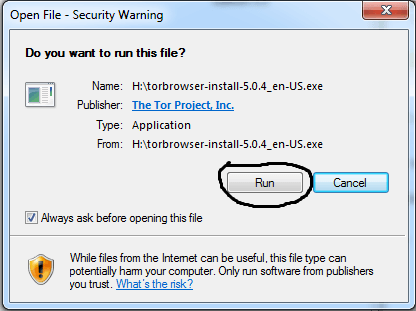
Start With The Basics: Preparing And Installing Tor
Research what they offer and assess your privacy needs to make a decision about which dark web browser works best for you. Tor is a powerful tool for enhancing your online anonymity, but it’s not a complete privacy solution. Learn how to set it up, explore what it does best (and where it falls short), and discover why pairing it with a trusted VPN could give you stronger, layered protection against prying eyes.
You don’t need special tools or a special browser like you need to access the dark web (more about that later). Anyone can access the deep web by using specialized search engines, dedicated web directories, and other sources that can help you find the data or information. Tor is slower than standard browsers because it routes your traffic through multiple servers.
If any link looks weird, it likely is and may be a phishing link. Don’t open attachments from untrusted sources, as they are a common vector for spreading malware. By default, Tor uses the Standard security level, but you can upgrade it to Safer or Safest. To use a new circuit, click the circuit button next to the domain. Then, click on New Tor circuit for this site, as illustrated below.
- Though it is not illegal to visit the dark web, accessing it can expose you to serious legal risks, even if you don’t have any criminal activity in mind.
- Only access the dark web with both a VPN and the Tor Browser active.
- Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity.
- Browsers with the appropriate proxy can reach these sites, but others can’t.
- I2P is a private network built for secure, anonymous communication.
Are Dark Web Browsers Safe?
As a matter of fact, your data could be anywhere on the internet, meaning it could already be at the three internet levels (surface web, deep web, and dark web). While a website can’t identify you or an ISP can’t decrypt your internet traffic; still, they can still see you using Tor, which can draw some unwanted attention and raise suspicions. DarkWeb “marketplaces” guarantee confidentiality and anti-surveillance for your online purchases that you simply won’t find on any other websites. Many turn to the dark to grab such medications with its private and secure networks. Some common pain relievers and sleeping pills available in the EU are illegal in various Middle East and Asia countries.
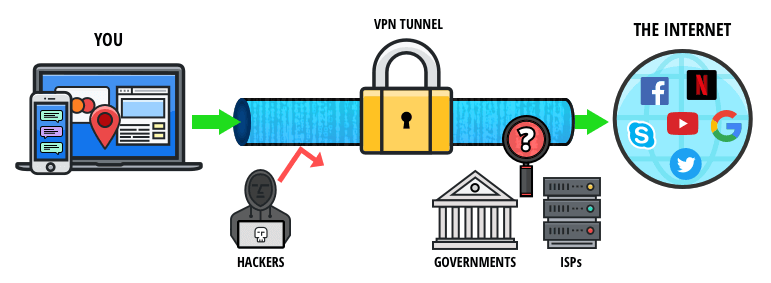
What’s The Difference Between The Tor Browser And A VPN?
It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections. However, using Tor has some challenges that you should be prepared for. With rising curiosity around hidden corners of the internet, many professionals wonder, “how to access the dark web” safely. From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents. Tor routes your traffic through a chain of relays to obscure your IP address. This makes it harder for websites, ISPs, or surveillance tools to see who you are or what you’re doing.
Regularly Update Your Software
We already went through VPNs, anonymizing web browsers, and disposable operating systems, so I won’t bother reminding you about those. For instance, if you want to buy a laptop or a smartphone, you can try your luck in one of these shops. Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”.
- Though people usually think of dark websites as the wrong online place, that’s not the complete truth.
- Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff.
- You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers.
- In practice, we found very little use of VPN Over Tor and saw no significant advantages.
Are Sites On The Dark Web Illegal To Use And Visit?
We’ll focus on secure, ethical practices tailored to cybersecurity professionals and IT leaders. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet. Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only. Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network. However, its network is still small, and there aren’t many hidden services available yet.
Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved. Hence, you never know when a popular .onion site is going to vanish, or even die. Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). The best thing is to actually understand how to find the fresh, new links. The good news is that the platform will not see what you copy/paste. Your data is encrypted in the Tor browser before reaching the ZeroBin servers.
About TorConnect
These secure communication platforms improve your security when using Tor. Practice safe, smart digital habits if you must use Tor to log into personal accounts. For instance, always use strong passwords that mix letters and symbols, making them hard to guess.
Explore this FAQ section to get answers to some common queries about this hidden part of the internet. Well, for one, each part serves a unique purpose and operates under varying levels of visibility and accessibility. Let’s discuss some more differences so you can easily distinguish them. It shouldn’t surprise you that your web activity is being monitored and recorded by a vast array of parties from your ISP on down.



