
These tools include for example different types of checkers, which assist threat actors in verifying whether the stolen card information they possess is valid and can be used to make unauthorized purchases. Cybercriminals are always on the lookout for new ways to use stolen credentials for generating income. And because people regularly store sensitive personal information across various online accounts without taking the extra measures needed to protect that information, cybercriminals have plenty to work with. Plug one hole, one exploit, and fraudsters will focus their efforts on a different one. Unfortunately, as long as cybercriminals continue to steal and then profit from our data, the underground economy will continue to flourish.

VPN Alternatives For Securing Remote Network Access
What is surprising to many is the deep web is 90% of the entire web, which is full of unharmful and legal items – they’re just not indexed for search engines. The opposite term of the deep web is the surface web, which is the internet we use every day. Where things get illegal is on the dark web – or black market, consisting of 6% of the web. The United States is a mecca for carders, simply because of the fact we are one of the last countries to rely on magnetic strip credit cards that are easily cloned and lack the security of newer chip and pin. The reason the U.S. is still using the technology from the 1960’s is a topic for another blog post altogether.
Navigating Ransomware Attacks While Proactively Managing Cyber Risks
The price for cloned cards varies depending on the credit limit, with an average price of $171. The three suspects from Indonesia confessed to stealing payment card data using the GetBilling JS-sniffer family. Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. Security researchers have been monitoring forums within the cybercriminal underworld to investigate the leading markets operating in 2024. Believe it or not, some dark web marketplaces have pretty advanced systems for building trust.

Why Buy Credit Cards On The Dark Web?
The first category includes classic marketplaces, which serve as one-stop shops for a wide range of illegal goods. These platforms sell everything from drugs and fake IDs to weapons and hacking tools, resembling a digital black-market bazaar. Wizardshop.cc was established in 2022, and offers a wide range of leaked CVVs, database dumps and even RDPs.

Most Popular
Since its inception, it has been attracting the attention of both old and new cybercriminal customers. Credit card information is the most commonly traded commodity in the hacking economy. This information comes in several flavors, with “CVVs” and “dumps” being the most popular.
- Tor’s Hidden Servers provide a real insight to an underground world that once was limited to dark alleys, shady places, and dangerous criminals.
- Axis Intelligence provides dark web surveillance solutions that help businesses identify leaked credentials, fraud attempts, and malware risks before they escalate.
- Discover the pros and cons of using credit cards or card for purchases, including benefits and risks, to make informed financial decisions.
- Journalists use the dark web to communicate with sources anonymously, and whistleblowers rely on it to share sensitive information without fear of retaliation.
- A new report has revealed that the B1ack Stash crime forum has just given away more than a million stolen credit cards for free.
It has a bidding feature, with new batches of stolen data being frequently added. It maintains a very strict level of user verification and integration with an official Telegram account to provide real-time updates to users. Various cryptocurrencies such as Bitcoin and Monero can be used to make purchases. The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown. Never log in with your real name or reuse passwords from other accounts. Stick to cryptocurrency, avoid downloading anything, and don’t share any personal info.

How Much Do Stolen Cards Cost On The Dark Web?
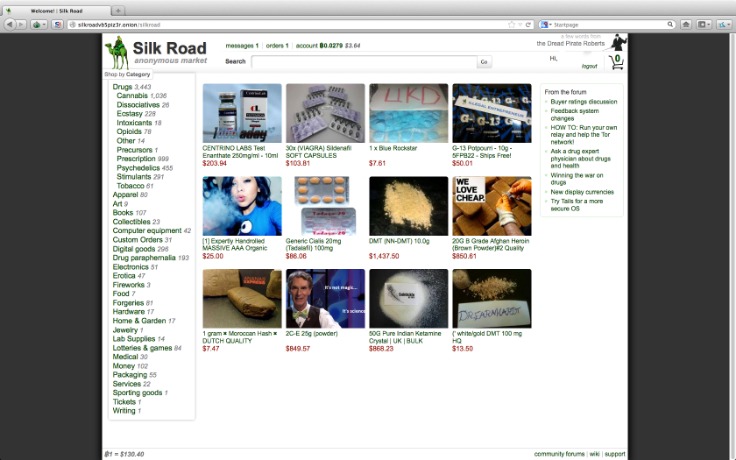
Cybercriminals looking to buy stolen information usually prefer Brians club stolen credit cards. Don’t ever reveal your true identity on the dark web marketplaces because there’s a high chance of hackers and scammers misusing it. Beware of sharing your financial details on the dark web, as this can result in identity theft and your bank account amount being stolen. The Silk Road was a famous dark web marketplace where users could buy and sell goods and services anonymously. All the payments were made through cryptocurrency, further enhancing marketplace anonymity. The users on this site can review and rate the products that promote reliable and fraudster vendors.
For fledgling criminals who don’t know how to use stolen credit cards, there are plenty of free and paid tutorials for carding on the dark web. BidenCash is another latest marketplace that started in 2022, and is now home to sensitive financial data transactions. This is where cybercriminals go to buy and sell things like stolen credit card numbers, personally identifiable information (PII), and even SSH login details. One thing that distinguishes BidenCash on the dark web, however, is how it markets itself. Card data is a hot commodity on the dark web, with credit card details and cloned cards being sold to cybercriminals. These stolen cards can be used for financial gain through unauthorized charges, account takeover, and identity theft.

Criminals Are Selling Millions Of Stolen Credit And Debit Card Numbers On The Dark Web
The dark web can only be accessed by users with specialized hardware or software. Users on the dark web are anonymous, and neither their behavior nor their IP addresses are monitored. The surface web, the deep web, and the dark web are the three main layers that make up the World Wide Web. You are most likely on the surface web when you conduct searches, read articles about growing lemons from websites, or shop for wedding accessories online. Crunching the available data, NordVPN says that of the 4,481,379 stolen cards, the maximum (1,561,739) belonged to US citizens.
The digital monetary system online is predominately operated by the likes of Paypal, Western Union, and banking companies that try to follow government regulations to prevent fraud and money laundering. There are two steps to legally take money and have it converted at the current Bitcoin rate into BTCs in our digital and anonymous bank. The type of information available on each specific card determines its price, with Visa cards having high credit limits typically selling at a higher price. All information, including rates and fees, are accurate as of the date of publication and are updated as provided by our partners. Some of the offers on this page may not be available through our website.
Together, We Hold Power To Account And Shine A Light On Government Transparency
Next, we will explore how to navigate the Dark Web and find reliable vendors to minimize these risks and protect against potential pitfalls. Having JavaScript enabled on the dark web can cause havoc because it can reveal your IP address to your website. Also, previously, the Tor browser was vulnerable to JavaScript attacks as it provided hackers a pathway to track your activities by using the session details. Therefore, for security reasons, disable JavaScript on the Tor browser and enjoy an anonymous browsing experience on the dark net. Despite using a VPN, there’s always a risk of the VPN leaking your IP address through DNS or WebRTC leaks or misconfigurations when on a dark web forum or marketplace.
Launched in 2020, Cypher Marketplace sells fraudulent documents, stolen credit cards, fake IDs, and malware. Its emphasis on user anonymity and document forgery makes it a core tool for identity fraud. When a hacker writes up new malware, steals a database, or phishes someone for their credit card number, the next step is often toward dark net marketplaces. These black markets allow buyers and sellers to make anonymous transactions using a combination of encrypted messages, aliases, and cryptocurrency. Dark web transactions play a key role in fund transfers for credit card fraud.
In this manner, the 2FA code given to the victim’s mobile device is rendered unavailable if an account has been entered into by a criminal. Payments Cards & Mobile is the go-to market intelligence hub for global payments news, research and consulting. Leveraging 15 years of data across 43 markets, our award-winning resources and expertise provide impartial, up to date analysis on the issues shaping the future of payments. “Clever hackers can significantly cut down how many numbers they need to guess and check to find your payment card number. In fact, researchers at Newcastle University estimate that an attack like this could take as few as six seconds,” note the researchers, adding that an average hacked card’s data costs less than $10. By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked data is exploited.
Physical cards are usually cloned from details stolen online, but can be used to withdraw from ATMs. Because the merchant requires equipment to clone the card and must send the buyer a physical product complete with PIN number, the price for cloned cards is much higher. This illegal market costs banks and cardholders millions each year.



