
It is important to highlight that participating in credit card transactions on the Dark Web is illegal and unethical. Engaging in illegal activities carries severe legal consequences and can harm individuals and financial institutions. This section is solely for informational purposes, and it is strongly advised to refrain from engaging in any illicit activities. Buyers must navigate through a labyrinth of fraudulent sellers and law enforcement operations targeting illegal marketplaces. It is crucial to exercise caution and take protective measures to safeguard personal information.
How Threat Actors Obtain And Trade Credit Card Data
The Hidden Wiki is one of the most well-known directories on the dark web, serving as a gateway for users looking to explore .onion sites securely and anonymously. The carding market overall recently surpassed more than $1.4 billion in sales with Bitcoin alone. Meanwhile, the operators behind UniCC will be seeking to cash out their formidable profits. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data. Established in 2022, Torzon market is one of the biggest and most diverse marketplaces on the dark web. It is considered very secure thanks to strict user validations and transparent payment and vendor review procedures.
Operating as shadowy corners of the internet, dark web credit card marketplaces facilitate the buying and selling of stolen payment cards. These platforms provide a marketplace for payment card data stolen by a variety of actors, leading to further specialization in crime. While criminals in the past might have stolen card data for their own reuse in carding, modern criminals split into those who capture and skim card data, and carders who take stolen card data and use it to make illicit purchases. Card Shops are a type of dark web marketplace that hosts the trade of credit cards and other stolen financial information. These platforms serve as hubs for cybercriminals to easily buy and sell compromised payment card details, including credit card numbers, CVV codes, expiry dates, and cardholder information. Carding shops are a type of dark web marketplace that hosts the trade of credit cards and other stolen financial information.
Credit Card And BIN (Bank Identification Number) Checkers
The release of this data poses significant risks for financial institutions and individual cardholders alike. The key is catching this activity before large volumes of card data make it to market. Dark Web credit card fraud is an ongoing problem and is not showing any signs of going away. That merchant specifically mentioned that using a stolen card on a store that uses Verified by Visa (VBV) will likely void the card. Verified by Visa is a service that prompts the cardholder for a one-time password whenever their card is used at participating stores. “It is conceivable that the data was shared for free to entice other criminal actors to frequent their site…by purchasing additional stolen data from unsuspecting victims,” according to the post (machine-translated from Italian).

By adding an extra layer of authentication, financial institutions reduce the risk of fraudulent activities during transactions. This proven technology, seamlessly working in the background, analyses transaction data and authenticates users in real-time, ensuring only legitimate transactions proceed. In the relentless battle against cyber threats, financial institutions must deploy proactive strategies and technologies to mitigate risks and protect customers, especially in the context of compromised credit card feeds. Additionally, securing transactions with a 3-D Secure ACS (Access Control Server) solution plays a pivotal role in bolstering the overall fraud prevention strategy. These aren’t just random forums, they’re organized platforms where stolen card data gets packaged and sold as “fullz” (full card details including CVV) or “dumps” (raw magnetic stripe data). You’re probably wondering how things like a PayPal account login or credit card details end up on the dark web.
The Fraud Files: What Is Fraud On The Darknet?
For journalists, activists, or anyone concerned about digital privacy, the Hidden Wiki serves as a gateway to information and tools that protect their identity and safeguard their online footprint. Hundreds of millions of payment card details have been stolen from online retailers, banks and payments companies before being sold for cryptocurrency on online marketplaces such as UniCC. These stolen cards have value because they can be used to purchase high-value items or gift cards, which can then be resold for cash.

Because the merchant requires equipment to clone the card and must send the buyer a physical product complete with PIN number, the price for cloned cards is much higher. AllWorld.Cards appears to be a relatively new player to the market for selling stolen credit-card data on the Dark Web, according to Cyble. “Our analysis suggests that this market has been around since May 2021 and is available on a Tor channel as well,” according to the post. Credit card details can be sold as digital items on the dark web, with the basics costing around $17.36. Physical cards, on the other hand, are cloned from stolen online details and can be used to withdraw cash from ATMs. The use of JavaScript-sniffers, also known as Magecart, has led to a significant increase in stolen payment card data.

Finding Dark Web Marketplaces
- Alongside the trade of credit card data on the dark web, complimentary tools named checkers are often offered and sold on the dark web.
- Rather than individual hackers working alone, the reality is that we’re dealing with sophisticated criminal enterprises that function like businesses, complete with customer service and quality guarantees.
- Thank you for joining us on this exploration of credit card transactions on the Dark Web.
- BidenCash shop was established in April 2022, following the seizure of other card shops and carding platforms by the Russian authorities.
- Early detection enables your security team to prevent a transaction, minimizing the risk of a chargeback.
- Connect to the VPN before launching the Tor Browser, ensuring all your traffic is routed through the encrypted VPN tunnel first.
You may not notice your credit card has been compromised until it gets declined or you start receiving monthly bills for transactions you never authorized. Stolen credit cards are also harmful to the businesses from which they were stolen in the first place. Customers whose payment information was stolen are less likely to want to continue doing business with your organization after a hack and your organization may sustain long-lasting reputational damage.

Secret Service, FBI, Dutch National High Tech Crime Unit, and cybersecurity firms like Searchlight Cyber and The Shadowserver Foundation, also resulted in the confiscation of cryptocurrency funds tied to illicit transactions. Now, the breach of a payment card network can become just the first step in a bigger scheme to encrypt a victim company’s data and hold it hostage. Group-IB’s data shows that individual card dumps rarely sell for more $1 million — and they have a limited shelf life, as victims eventually cancel compromised cards. Phishing is a method used by scammers to trick users into trusting them and providing their personal information or account data. We will also share some effective safety tips and discuss how virtual cards can help protect you from card fraud.
Fraud Detection Systems
In December, USA Today reported there had been an estimated $36 Billion USD stolen across U.S. unemployment benefits. Swiping may also refer to the process of using stolen debit card information to collect cash out of an ATM. Variations of this process have been popularized across deep web enthusiasts in the hip hop culture spurring a completely new genre of “scam rap” where the technique is woven into the lyrics of rap songs. DarkOwl has observed this with young scam-rappers such as Teejayx6, as shown in the video below.
- The first category includes classic marketplaces, which serve as one-stop shops for a wide range of illegal goods.
- The resulting financial loss from stolen information is tremendous, not only for the individual victim but also for the financial provider and any involved organizations.
- In addition to its main log-sharing function, Observer Cloud provides custom-built programs, a scam list, and chat groups for discussions and transactions related to logs.
- In addition we continuously monitor hundreds of Telegram channels and other parts of the ecosystem to proactively help prevent fraud.
- Additionally, securing transactions with a 3-D Secure ACS (Access Control Server) solution plays a pivotal role in bolstering the overall fraud prevention strategy.
Since late May 2021, the threat actor has been actively advertising and promoting the new platform on different Dark Web hacking-related platforms. The current leak of one million credit cards by the threat actor appears to be another marketing move to attract potential clients from hacking and cybercrime forums and increase the platform’s popularity. In early August 2021, a threat actor known as AW_cards published a data leak containing details of approximately one million stolen credit cards on several Dark Web hacking forums. The leak was shared free of charge as a promotion to the threat actor’s new carding marketplace, named AllWorld Cards.
❓What’s The Difference Between Fullz And CVV?
Sometimes hackers will commit “card-present fraud” by breaching the point of the sale at a physical store. Or they’ll commit “card-not-present fraud,” by hacking a website and stealing the online card information that gets entered into the checkout page. Learn the basics of credit card cards, including features, fees, and rewards to make informed decisions about your credit card usage. The price for cloned cards varies depending on the credit limit, with an average price of $171. These groups often originate from leaked credit card credentials, which have become a common phenomenon, particularly in the past months.

Joker’s Stash, A Forum For Stolen Data, Says It Will Shut Down Within 30 Days
Quality and validity of the data it provides justify its higher cost over other marketplaces. The platform’s popularity continues to grow, attracting both new and returning customers. Judging from the activity on the shop, BidenCash appears to be thriving in 2023, providing an active data and money exchange platform in a market that has experienced a decline in recent years.
How To Protect Your Identity While Browsing The Dark Web
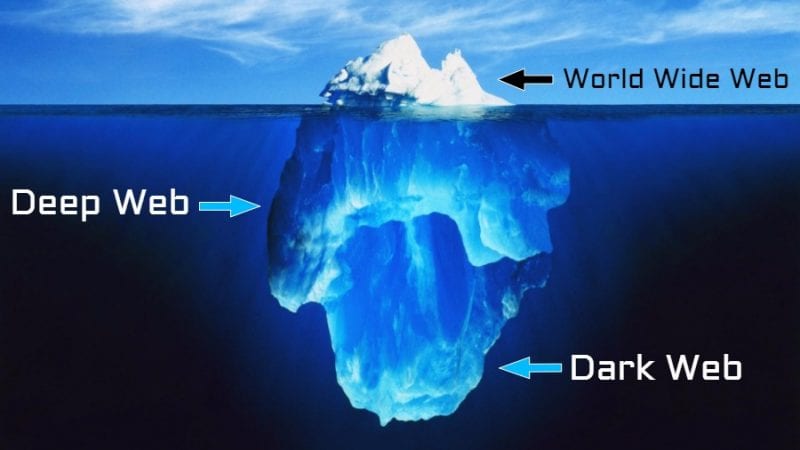
This includes password-protected sites, private databases, academic journals, and, notably, dark web services accessible only through networks like Tor or I2P. The Hidden Wiki is a gateway to these deep web resources, offering links to .onion sites that cannot be found via Google or other surface web search engines. Thus, users who want to explore hidden, uncensored, or private content often rely on tools like the Hidden Wiki because it provides structured access to resources beyond Google’s reach. Dark web marketplaces remain the backbone of many users’ dark web experience, providing anonymous platforms for buying and selling goods and services that range from digital products to physical items.
Proven Ways For Online Gamers To Avoid Cyber Attacks And Scams
As one of the prominent platforms supporting such activities, card shops make carrying out such scams relatively easy and popular. The group also facilitates connections between buyers and sellers, with some members offering daily-updated data sources and private datasets for a fee. Over time, EMP/mailpass/sqli Chat has established itself as a long-running discussion channel where cybercriminals exchange knowledge, trade illicit data, and promote underground services. Clicking a bad link on the dark web can expose you to phishing scams, malware infections, or honeypots set up by law enforcement. These malicious sites may attempt to steal your personal information or compromise your device’s security. If you suspect you’ve clicked a dangerous link, immediately disconnect from the internet, run a full malware scan, and change any passwords that may have been exposed.



