The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web.
Strategic AI In Cyber Defense: How To Stay Ahead Without Increasing Risk
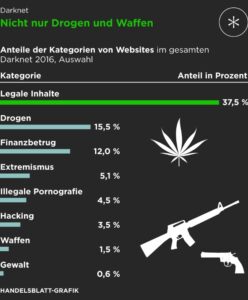
From stolen credit cards and hacked PayPal accounts to hard and soft drugs, pirated copies of all kinds, and weapons — there is nothing that is not offered on the darknet. Payment is usually made with Bitcoins, as the digital currency promises maximum anonymity and the payment flows are untraceable. It contains many distinct spaces catering to a wide range of activities, from meritorious to abhorrent. In this sense, the darknet is no more dangerous than the rest of the internet. And darknet services do provide anonymity, privacy, freedom of expression and security, even in the face of a growing surveillance state.
Darknet Market Links ( Official )

Users typically need to access the darknet using specialized browsers like Tor. Onion sites are hosted on a web server in the same way as ordinary sites, but you change web server configurations so that it only responds to your localhost. Then, you configure Tor to designate it as a Tor service, which will give you an onion link to your site. The CIA launched a site on the dark web in 2019 to give people a secure way to contact the agency and report information. The reliance on Bitcoin has proven to be a game-changer, as its decentralized nature eliminates the need for intermediaries, reducing transaction costs and increasing speed. Additionally, the integration of privacy-focused cryptocurrencies, such as Monero, has provided users with even greater anonymity options.
What Kinds Of Products And Services Do Legit Darknet Vendors Offer?

Accepted currencies are Bitcoin and Monero although Revolution intends to move to Monero exclusively. There, you’ll find a society that lurks intentionally in the blind spots of search engines. All call it hard to reach—though it’s hardly impregnable, given last week’s news of security vulnerabilities, as well as site takedowns following the arrest of an alleged pornographer. Like a demilitarized zone or a lawless land, it’s not a place most people visit—nor should they.

The dark web may also be put to good use by whistleblowers, who can leak classified information on the dark web using websites such as Wikileaks. Operating Tor is largely similar to operating a web browser such as Mozilla Firefox or Google Chrome. Special tools–the Tor Browser or the Invisible Internet Project (I2P) network–are needed to overcome these obstructions.
Darknet Markets On Reddit: A Comprehensive Guide
These markets are accessible only through the Tor network, which allows users to browse and transact anonymously. Darknet dating sites offer a unique and often controversial experience for users seeking love and companionship. While these sites may provide a sense of freedom and anonymity, they also come with significant risks, including the potential for fraud, harm, and lack of legal recourse. As with any online platform, it is important for users to exercise caution and use common sense when engaging with others on darknet dating sites. The Reddit Darknet Market List 2024 is a community-driven resource that provides a comprehensive list of the most popular and reputable darknet markets.
Legitimate Use Cases For The Average User
If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. To determine if a darknet marketplace is legitimate, look for reviews and feedback from other users, and check to see if the marketplace has been around for a while. Legitimate marketplaces will have a clear and detailed list of products and services, as well as clear policies for buying and selling. The shutdown of the /r/DarkNetMarkets subreddit on March 21, 2018 was a major blow to the online black market community.
How Do I Access The Darknet To Find Legit Darknet Vendors?
Patterns recommended to avoid include hiring hitmen like Dread Pirate Roberts, and sharing handles for software questions on sites like Stack Exchange. Generally, complete anonymity and invisibility to the search engines are the two essential features that define the darknet. Despite the common assumption, its use is not limited to buying and selling illicit products. The growing popularity of these platforms is driven by their ability to offer a wide range of products, from pharmaceuticals to recreational substances, catering to diverse user needs. The use of darknet market lists and URLs has further simplified navigation, allowing users to quickly find trusted vendors and products.
Tor’s network doesn’t just offer anonymity to Web surfers, though; it also offers anonymity to Web servers, in the form of Hidden Services. Many countries lack the equivalent of the United States’ First Amendment. Darknets grant everyone the power to speak freely without fear of censorship or persecution. That said, three common Onionland starting points are The Hidden Wiki, TorDir, and TorLinks. All the directories in Onionland always point to Torch as a search engine of onions, but it never works properly. You can get to Torch’s front page just fine, but individual searches time out.
This focus on security has contributed to the growing trust in darknet markets, attracting more users and vendors each year. The diversity of offerings on darknet markets has expanded significantly, catering to a wide range of user preferences. From pharmaceuticals to recreational substances, these platforms provide detailed product listings, user reviews, and vendor ratings, ensuring transparency and reliability. The improved interfaces of top darknet markets in 2025 make navigation intuitive, allowing users to quickly locate desired products and complete transactions with minimal effort. As darknet markets continue to evolve, they are expected to offer even more sophisticated tools and features, further enhancing their appeal to users.

As to security and anonymity, marketplaces guarantee their users’ privacy and protection, which provide threat actors with a safe and optimal environment for their illegal activities. It has gained a lot of users and has become a popular marketplace due to its focus on security. If you go premium, you’ll lose the ads and gain additional data insights and access to historical versions of websites. The reliability of R darknet markets cannot be guaranteed at all times, as they may be susceptible to DDoS attacks. However, I will strive top darknet markets 2023 reddit to update this post with working links.
“Seasonal scams continue to exist because they’re successful for hackers. Cybersecurity leaders should take steps to bulk up defenses during the holidays, when there is heightened email activity and emotions that social engineers can manipulate,” said Hoxhunt CEO, Mika Aalto. Stolen data, such as compromised gift cards and credit card details, are also in high demand, fueling an ecosystem that preys on shoppers’ eagerness for deals. Cyble noted that the accounts linked to the exposed credentials are hopefully protected by other security layers, such as multifactor authentication (MFA). The Cyble researchers did not attempt to determine whether any credentials were valid. However, many were related to easily accessible web console interfaces, single sign-on (SSO) logins, and other web-facing account access points.
- A look with the Tor browser at a darknet directory such as the uncensored Hidden Wiki reveals that seemingly anything goes on the darknet.
- However, Silk Road 2.0 quickly took up the limelight and relaunched, and not long after that was taken down, Silk Road 3.0 popped up, and that’s where we are today.
- When surfing the surface web sites using the TOR browser, your real IP address will be concealed and your connection will seem to originate from the TOR Exit relay IP address instead.
- Technically, it is always possible to infer user identity from their social interactions and group socialization process with other people (Al Jawaheri et al. 2020; Biryukov et al. 2013).
These platforms also employ escrow systems and vendor ratings, which significantly reduce the risk of fraud and ensure that transactions are completed smoothly. Bitcoin remains the primary currency for transactions, providing a seamless and secure payment method. The integration of multi-signature wallets and escrow services further minimizes risks, ensuring that both buyers and sellers are protected throughout the transaction process.
“However, the leaked credentials underscore the importance of dark web monitoring as an early warning system for keeping such leaks from becoming much bigger cyberattacks,” the researchers added. They were likely pulled from infostealer logs and then sold on cybercrime marketplaces in bulk for as little as $10. CRIL analyses the darkweb marketplace’s deceptive practices, the recent arrest of an Incognito administrator, and the SuperMarket wallet heist. AI-driven cyberattacks are rising in Australia, with 50+ threat groups active in 2025 and a 13% spike in major incidents across key sectors. Many users surf the dark web due to its greater privacy levels compared to the regular internet, AKA the ‘clear web’. In addition, it has an automatic kill switch (Network Lock) that stops traffic if the VPN connection fails.